Adding Hosts
It is very easy to add hosts to Sandfly. Simply paste in the hostnames, IP addresses, or IP netblocks that you want to add. It takes Sandfly roughly 1-2 seconds to connect to a host, inventory the system, and return results. Therefore, many hosts can be added very quickly to get immediate protection.
Here you can see the full screen for adding hosts. Further below we will go over each section in more details.
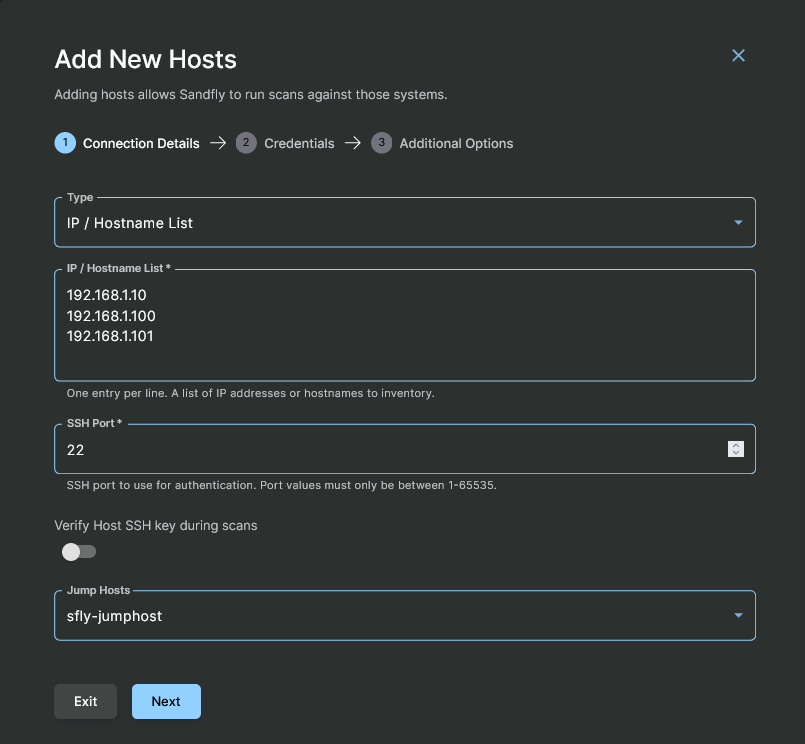
Adding Hosts to Sandfly
Host Details
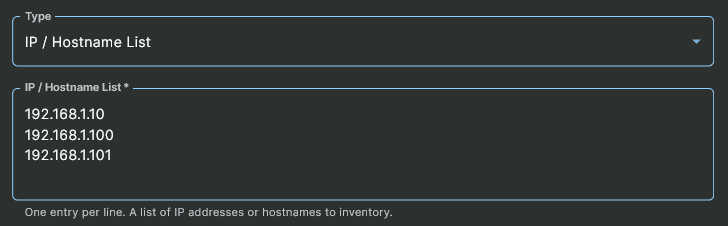
Adding by IP / Hostname List
In order to add a list of hosts for protection, first set the Type to the IP / Hostname List option. Then enter into the IP / Hostname List textbox, one entry per line, either an IP Address or Hostname of a host that would be reachable via SSH at the indicated port from the Sandfly node(s) or jumphost(s), as appropriate for your network architecture.
Either a partially or fully qualified Hostname can be used in this list. However, the hostname must be DNS resolvable on the Sandfly server.
Selecting IP List or Range
Adding by IP Address Range
Alternatively, if you have a group of hosts on a netblock that needs protection, Sandfly can easily look for them without the need to enter hosts individually. First, set the Type to the IP Netblock List option. Then, in the IP Netblock List textbox enter one or more netblocks, one entry per line, up to a class B network in CIDR notation (e.g. 192.168.1.0/24).
IMPORTANT: Netblock Scanning is Limited to Class BSandfly can accept up to a Class B network at a time (65535 hosts). If you need to scan more than this, you will need to enter each net block in as separate entries.
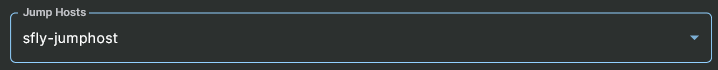
Add Jump Host (optional)
If you are using a jump host to connect to these systems, they can be selected in this section. At least one jump host must already be setup to show options in the Jump Host drop down. If a jump host has not been setup yet, please refer to the Jump Hosts documentation on how to do this.
Optional Jump Host Selection
Add Credentials
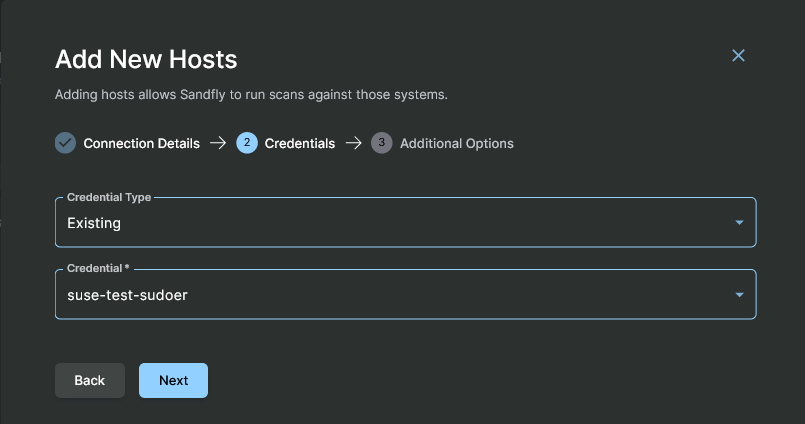
Use Existing Credentials
In the next section, select the credential you want Sandfly to use to login to these hosts. This is the credential you setup as detailed under the Host Credentials area. If a credential is invalid, Sandfly will indicate this to you when you view the list of hosts.
Selecting a Credential to Use
Use New Credentials
If you have not yet added any credentials to pick from, it can be done at this step. Select New for the Credential Type and fill in the fields for the SSH key or username/password to use.
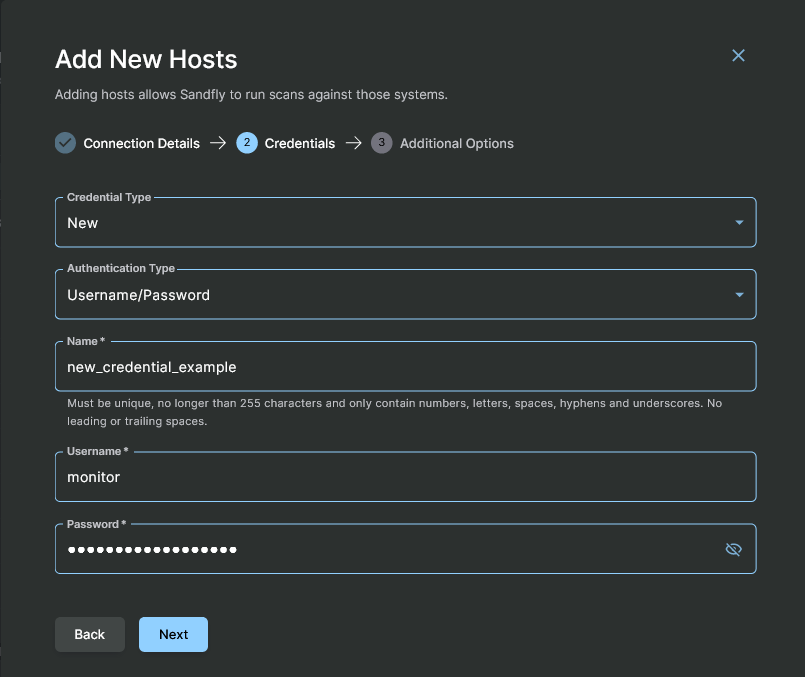
Adding Hosts with New Credentials
Additional Options
Select Queue
For the last section, Sandfly can use named queues to send the host add request to an appropriate node. For instance, you may have a node running inside a protected segment in Amazon Cloud, another at DigitalOcean, and a final one internally. If these nodes are all online you will get a drop down option with their names. The default name is main if you have not enabled this feature on your Sandfly nodes.
The (parenthesis) after the queue name indicates how many nodes are servicing that queue. Below we see a queue name of main with two nodes active.
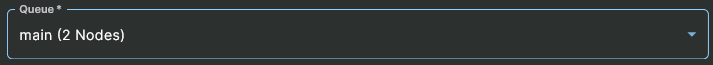
Selecting Named Queue for Scanning
Add Tags (optional)
Host tags can optionally be added via this field. If you are uncertain as to what to use in this form, they can be easily added or removed later, at any time. These tags come into use by other features that target hosts by their tags or for filtering / displaying host data.
Advanced Options
Override Scan Directory (optional)
The working directory that Sandfly normally uses to upload the agent to and run from is controlled by the node’s default_directory option.
On occasion there may be the need for a single host, or a certain type of hosts, which requires a different directory. The most common reasons are when the targeted directory is read-only or its file system is set to "noexec". For example, Cisco NX-OS switches need to use /volatile, but for other reasons, Sandfly cannot change the sandfly user’s home directory to something under /volatile.
If this field contains a non-empty value, then the node will only use that overridden location instead of the node’s configured default and fallback directories.
If you want the override scan directory to be the user’s home directory, which you would typically get by configuring the node with an empty string, use ~ as the value. The node will understand that to refer to the home directory of the user.
Finish
Once all of the data has been entered, click the Finish button. Behind the scenes, Sandfly nodes are now attempting to connect to the list of addresses via SSH and collecting host inventory. After a few seconds, the Refresh button can be hit and hosts will start to appear.
The list will show all active and inactive hosts. You are now ready to scan the systems for Linux threats.
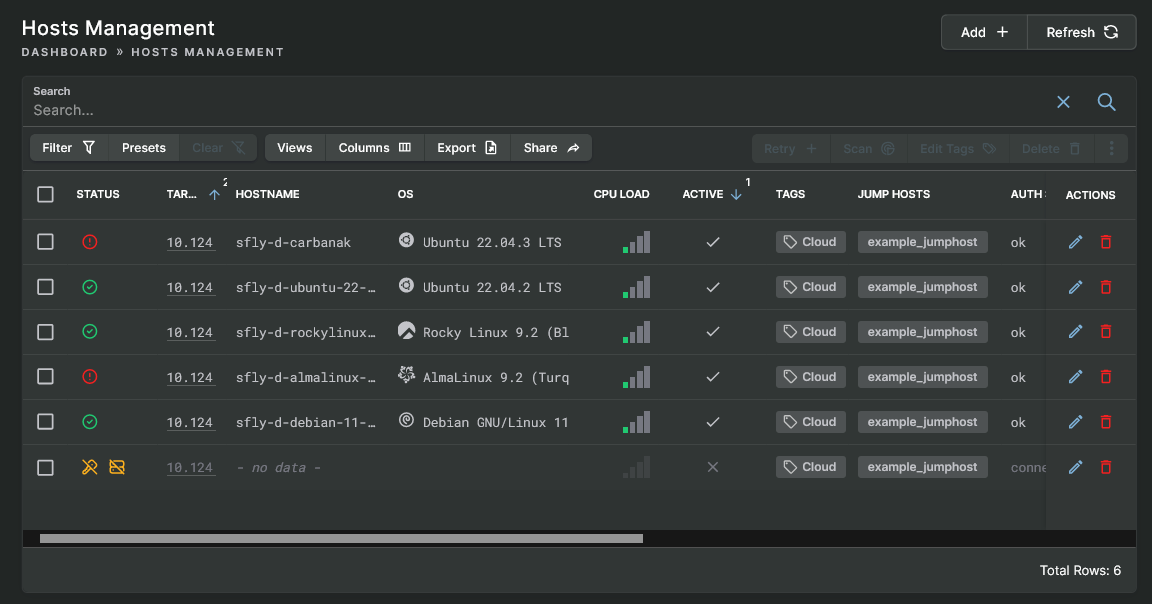
Hosts View
Finding Unknown Hosts with IP Range Scan
If you want to search for hosts that are on your network, Sandfly can look for them with an IP Range scan. This feature is useful for admins trying to get a handle on what systems exist on their network, or for incident responders that may be entering a hot incident site blind so as to be able to see all the devices that may exist.
For instance, referring to the image above, a host within the netblock of 10.124.100.0/24 was found, but with a connection error. These kinds of unknown hosts are common. Other times you may find hosts that can connect to SSH, but time out or have an exception error. This is valuable information to know when assessing a network.
To search unknown devices, enter at least one netblock, one entry per line and in CIDR notation (e.g. 192.168.1.0/24) up to a class B. Sandfly will use the supplied credentials and try to authenticate via SSH to any device it finds with an open SSH port. If it logins successfully, it will inventory and add the host like normal. Otherwise, the entry will not be marked as Active, initially shown with a Status of Inactive and it cannot be scanned by the sandflies.
IMPORTANT: Netblock Scanning is Limited to Class BSandfly can accept up to a Class B network at a time (65,535 hosts). If you need to scan more than this, you will need to enter each net block in as separate entries.
If Sandfly saw a host, but could not log in, then you will see authentication failures in the host view. This is not fatal, but more informative that a host is present but could not be accessed. You can try to access these hosts with another credential or delete them if you do not want to Sandfly to try accessing them.
CAUTION: Sandfly Adding Hosts and Network TimeoutsIf you have a lot of dead addresses when you scan a netblock (or packet filters that drop packets on remote hosts), Sandfly may take some time to complete waiting for dead connections to timeout.
Each scanning node has 500 threads. This can impose a large load on a network if you run a number of scanning nodes and enter many blocks of IP addresses. It is possible to scan several thousand systems at once which could cause problems. We recommend you space out your scans to prevent this.
Updated 26 days ago