Hosts Management
Host registration is a prerequisite for Sandfly protection. Users can manage the system lifecycle by adding, viewing, or deleting hosts in Hosts Management.
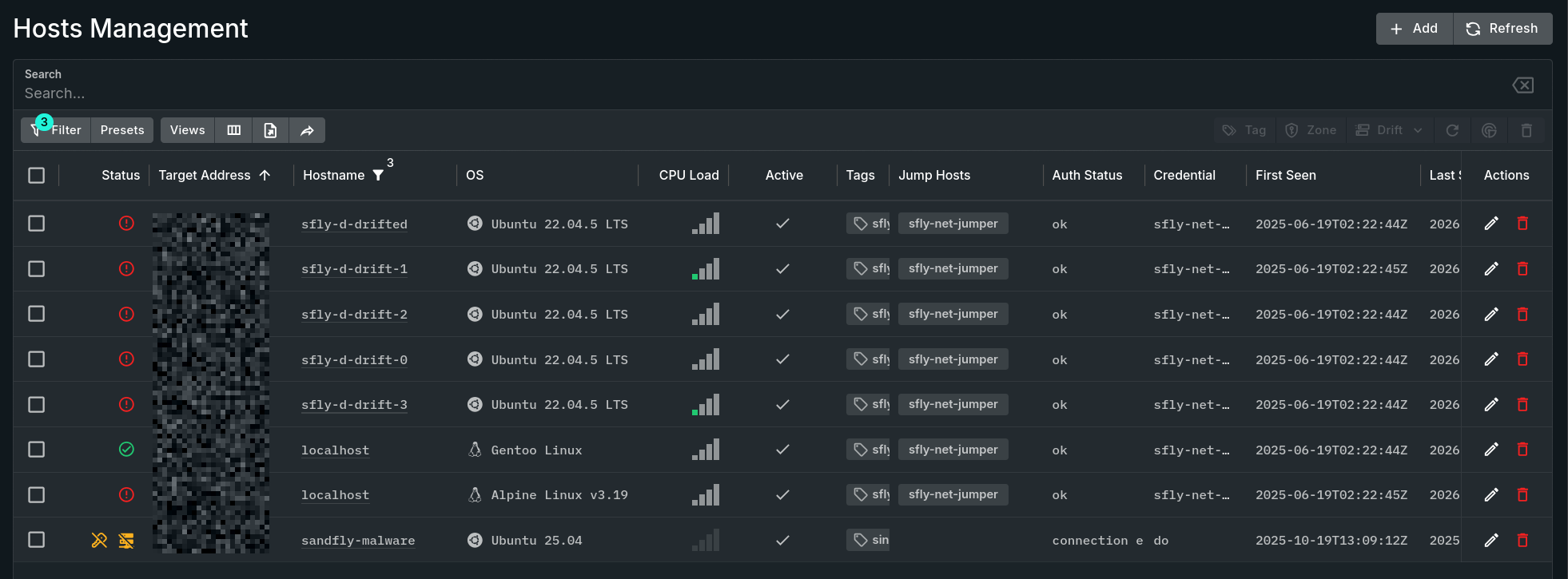
Host Management Page
Updated about 1 month ago
Host registration is a prerequisite for Sandfly protection. Users can manage the system lifecycle by adding, viewing, or deleting hosts in Hosts Management.

Host Management Page
Updated about 1 month ago