Sandfly Hunter
Sandfly Hunter is a way to quickly search for common pieces of threat data that may be present on your hosts. This is a powerful feature of Sandfly which can help find and see threats against your systems quickly.
Hunter Concepts
Sandfly Hunter allows you to click on critical forensic attributes in an event and see what other systems have the same attribute present. Sandfly is able to search for a variety of attributes in Hunter mode such as:
- Process attributes such as names, paths, cryptographic hashes and owners.
- File attributes such as names, paths, cryptographic hashes and owners.
- Directory attributes such as names, paths and owners.
- Username attributes such as home directories, group memberships and UIDs.
- User password attributes such as password type and search hashes (a hash of the password hash that allows you to search across hosts without exposing the hashed password to operators).
- SSH keys such as key types, key data and key hashes which can be used to search across hosts for identical SSH authorized_keys entries for identical keys in use elsewhere.
Recon Sandflies
To get the maximum benefit from the Sandfly Hunter mode, we recommend that you do not disable the recon sandflies which are enabled by default. Those modules collect process, user and other data and save it in the database each time a host is checked. This data will be available to future searches if needed and builds a timeline of events if a host is compromised so you can see what and when a problem happened.
For instance, the recon_process_list_all Sandfly will collect all running processes every time the host is checked. This data will be stored and you will have a running record of all processes we saw at the time. Later, if you run into a suspicious process, the Sandfly Hunter data will pull up these historical records to show you where else we saw these processes.
There are other disabled recon modules that pull additional data such as file attributes from system /bin and other directories. You can enable these at your discretion, but keep in mind that they may generate a lot of data that your database will need to be scaled to store.
Recon data will be stored as passed events in the database. When Sandfly Hunter does a search, this data will be used to help form a more complete picture of what may be going on.
Hunter Timeline
With each forensic attribute selected, you will be taken to a screen that shows all systems where that attribute has been seen and what times they were it was first spotted.
A Suspicious SSH Key
For instance, the image below is the result of a search where we found authorized keys2 files that generated an alert on several systems. That file was pulled into the forensic data and when we clicked on the key's sixth sha512 hash entry we immediately see a list of hosts of where the matching key is present.
Alerts show up as red bars on the timeline. If there were pass results, they would appear as green bars on the same timeline.
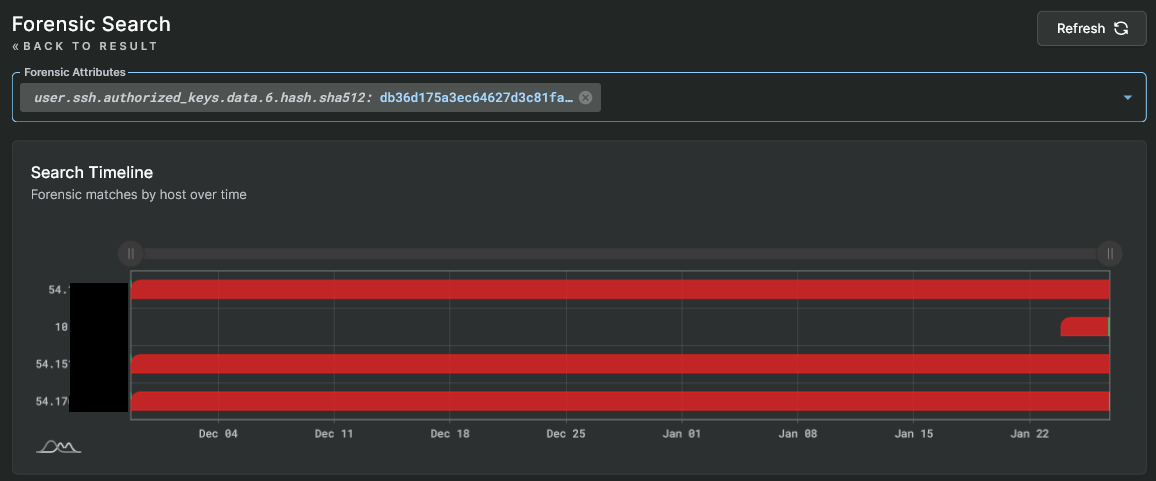
SSH Key Hunting
In the example image above, the "54." hosts (i.e. the first, third, and fourth rows), have detected the presence of that file for over a month. Those three hosts may be temporary exceptions or being actively monitored for the alerts to continue to exist. However, two days ago the same key shows up on another host that is not on the same network.
From a threat hunting point of view you now have a suspicious key and you can immediately see all of the hosts which have that key. This ability can aid you to quickly locate hosts that need to be investigated in case an attacker is using the key to move laterally but has not activated any alerts yet.
A Suspicious Process
Next, we find a host with an alert for a suspicious network process running the SCTP protocol. This is extremely dangerous and a look at the forensic data shows a command line that is very odd.
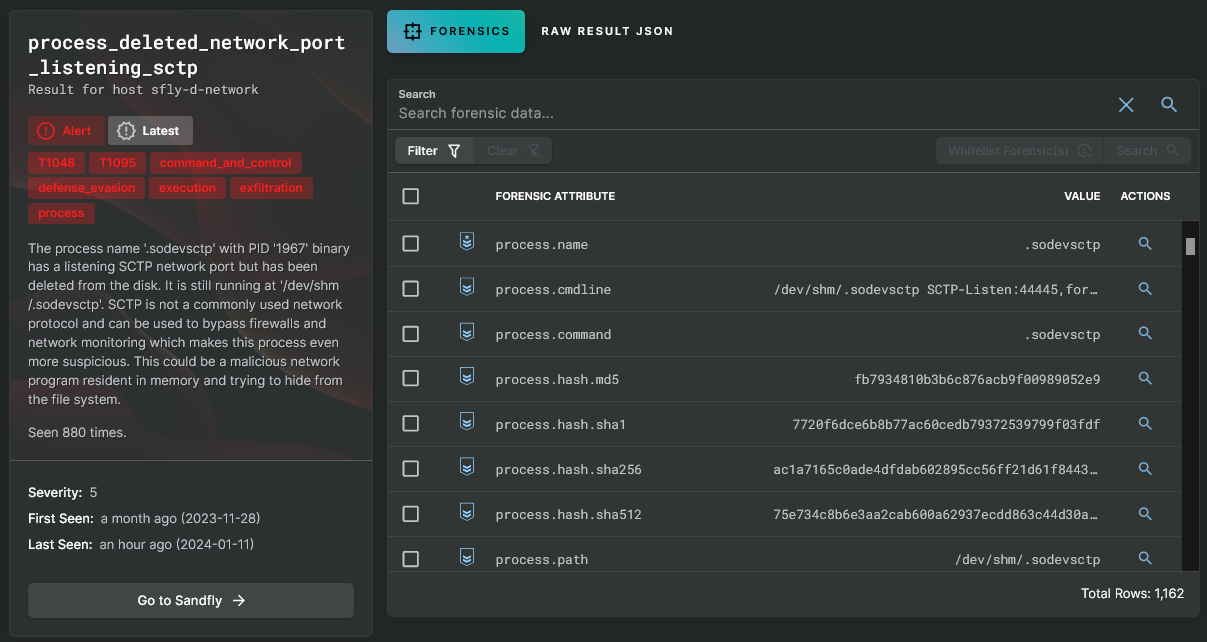
Sandfly finds a SCTP backdoor process
We quickly click on the process.hash.sha1 field and jump to Sandfly Hunter mode. Here we see that same process hash is running on two hosts and each host has identical alerts. The malicious process is contained to these two hosts and we can begin isolation and incident response procedures.
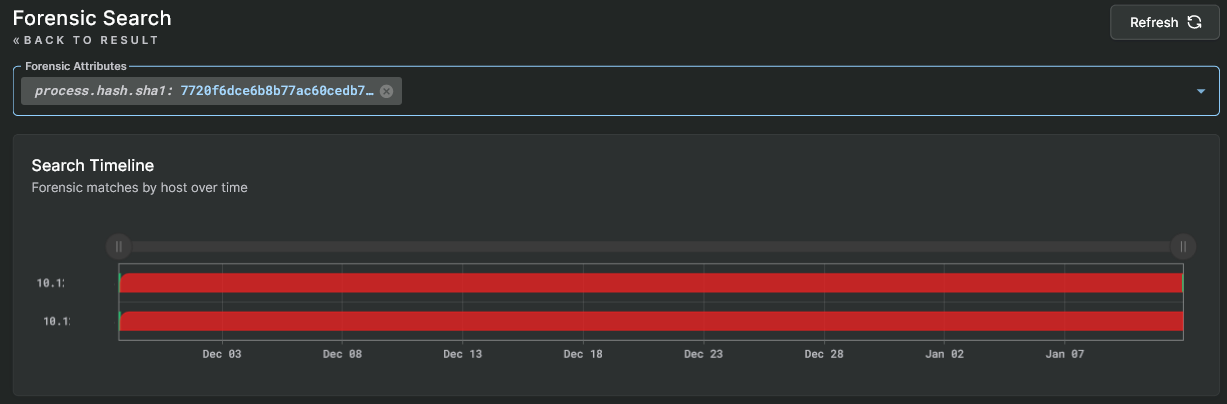
Sandfly Hunter SCTP backdoor found on two hosts
Recon Sandflies Collect Supporting Data
You will notice that some of the alerts are green. This is normal because they are attributes found during the recon_process_list_all checks Sandfly performs. These are reconnaissance checks where Sandfly pulls all system process data and simply saves the results. Although not a security check, the resulting forensic data is now available for searching if needed.
Recon and Alert Sandflies Build Timeline View
The recon checks show that similar process hashes were running on the hosts without alerts likely because they were legitimate. But suddenly the process was seen doing something suspicious and this generated the alert only recently.
In fact, in the timeline view we see above the red alerts happened just 8 minutes prior where the full 72 hour window showed nothing unusual. This indicates the host was recently compromised with the suspicious use of this process only showing up now.
Viewing Results
Under the Sandfly Hunter you can click on each row and see the individual alert details just as you can in normal results view.
Updated about 1 month ago