Viewing Results
Viewing Results
Sandfly constantly looks at your hosts for signs of compromise or other suspicious activity. Anything it finds is reported as an alarm for you to view and take action. Sandfly also keeps track of every time it checks a host and found that it passed the check. This works as an auditing platform to show you the last time a system was checked and found to be clean.
Viewing Alerts
Alerts are shown in a list view along with other supporting data which varies depending on the Results type selected. Here we see the list from the All Results option:
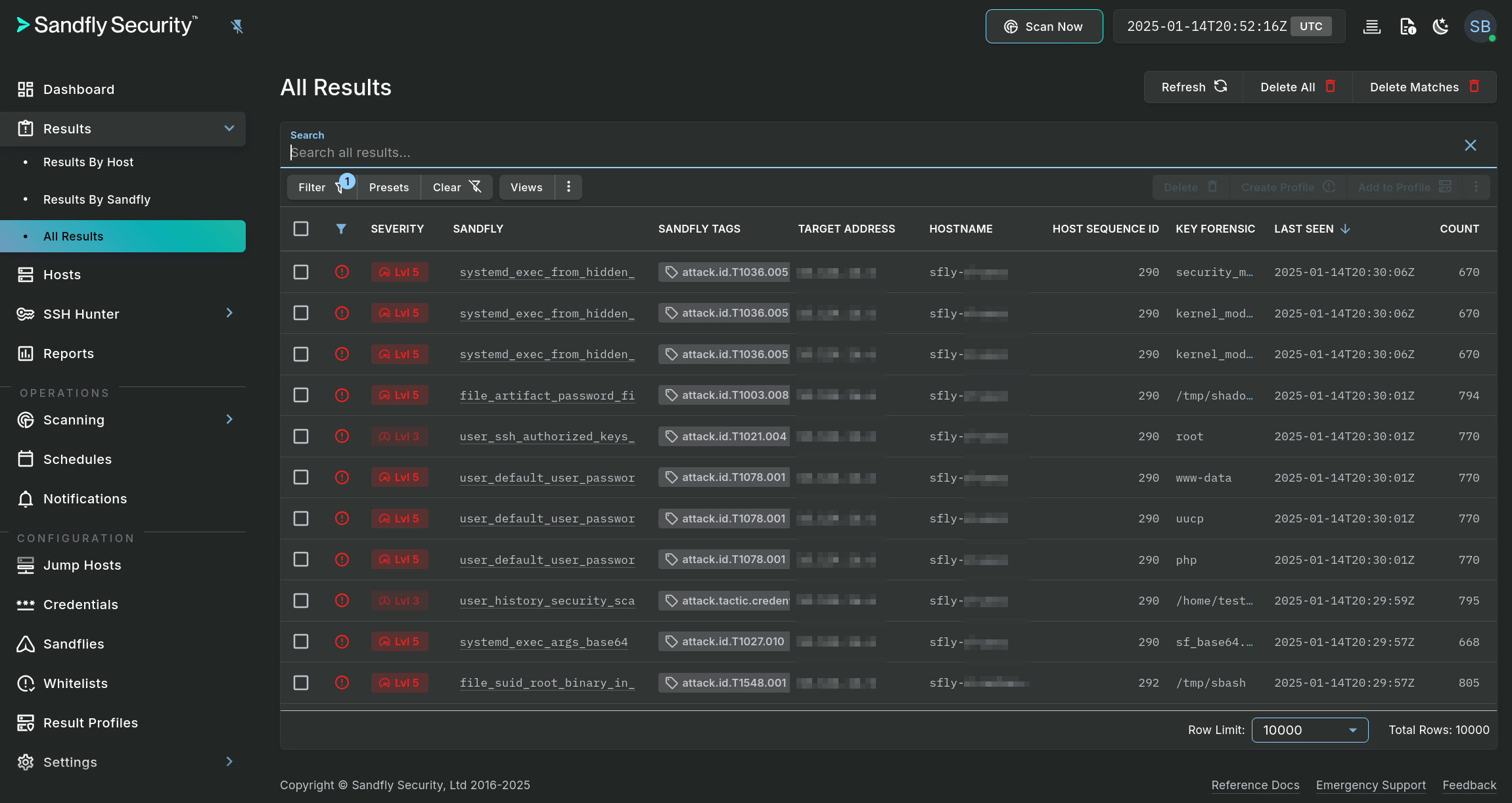
Hosts with Alerts
To view details of a result, simply double click on a row in the table or single click any hyperlinked data element. This action will open a pop-out panel which contains all of the information for that result.
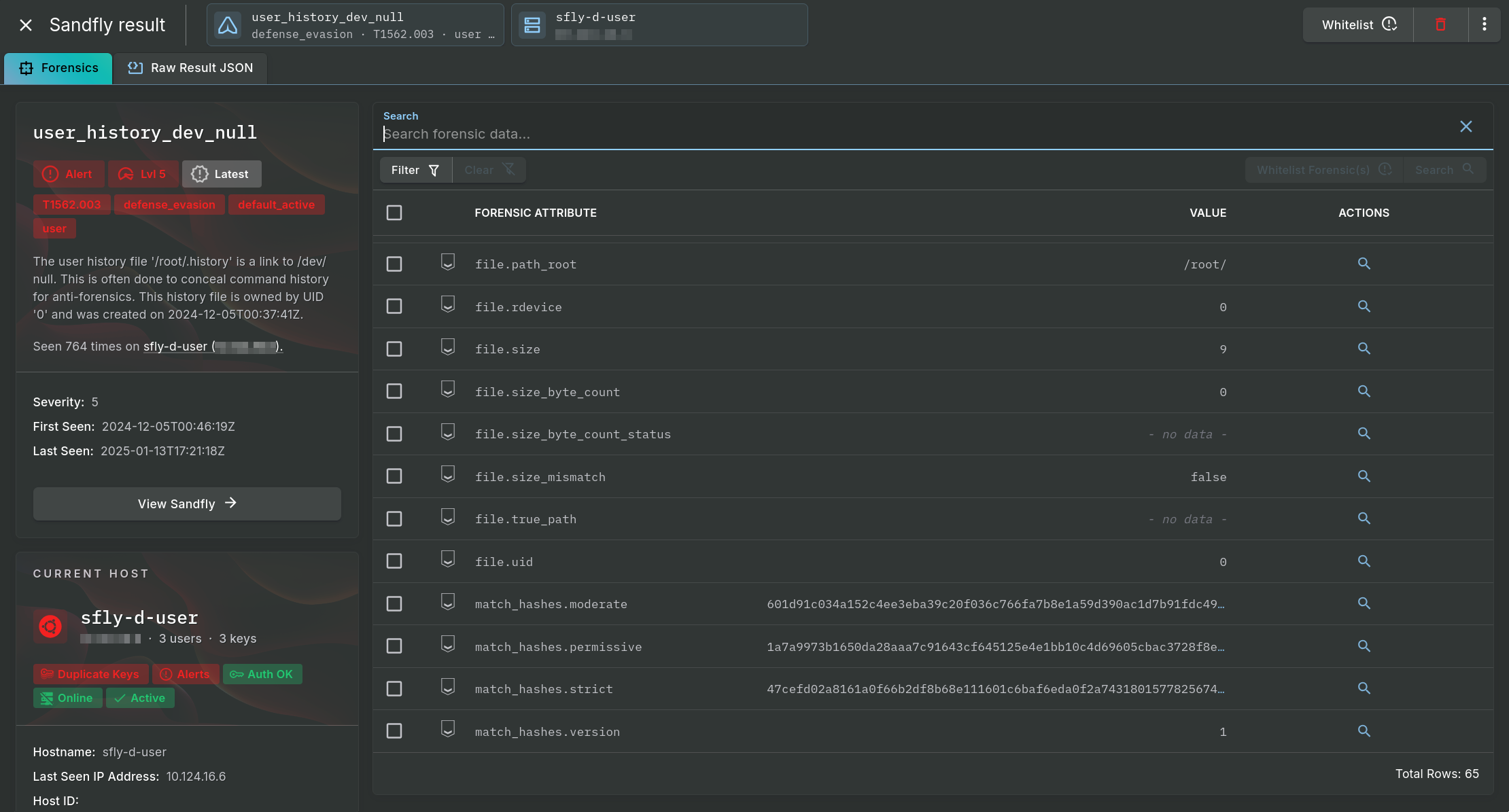
Complete Forensic View
Raw result data can be accessed by selecting the Raw Result JSON tab. From there the JSON data can be either downloaded via the Download button, copied in its entirety via the Copy button, or select and copy any desired portion of the textual data as needed.
All available AI analyses for an associated result can be displayed by selecting the AI Analysis tab.
Forensic Data Viewer
The forensic data view of an alert has details that include information such as the affected target name, first and last seen dates, and severity. Additionally, you will see an explanation in plain English about what was found.
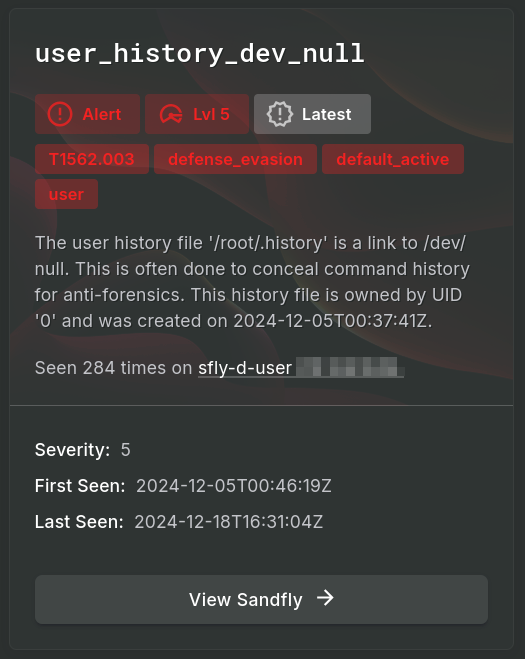
Mitre ATT&CK® Details
Along with the alert information you will have links to the Mitre ATT&CK tag(s) that the attack falls under. Clicking on a tag will take you to the Mitre ATT&CK page describing the tactic in more detail.

Mitre ATT&CK Details
Along with the high-level tactic type, Sandfly will provide a specific ATT&CK ID of the tactic if one is available in the Mitre database.
Result Host Summary
Below the explanation data section is a summary view of the host. Clicking the View Host button takes you directly to the registration data where the full details of that host can be seen.
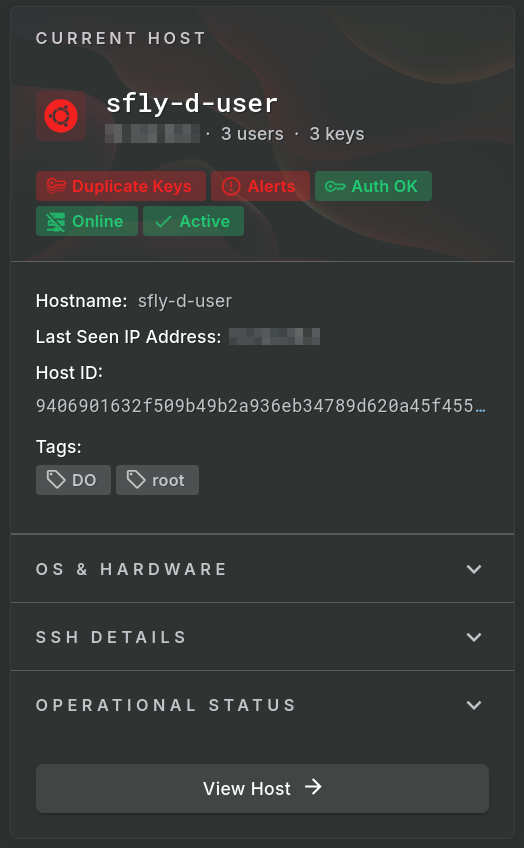
Host Summary
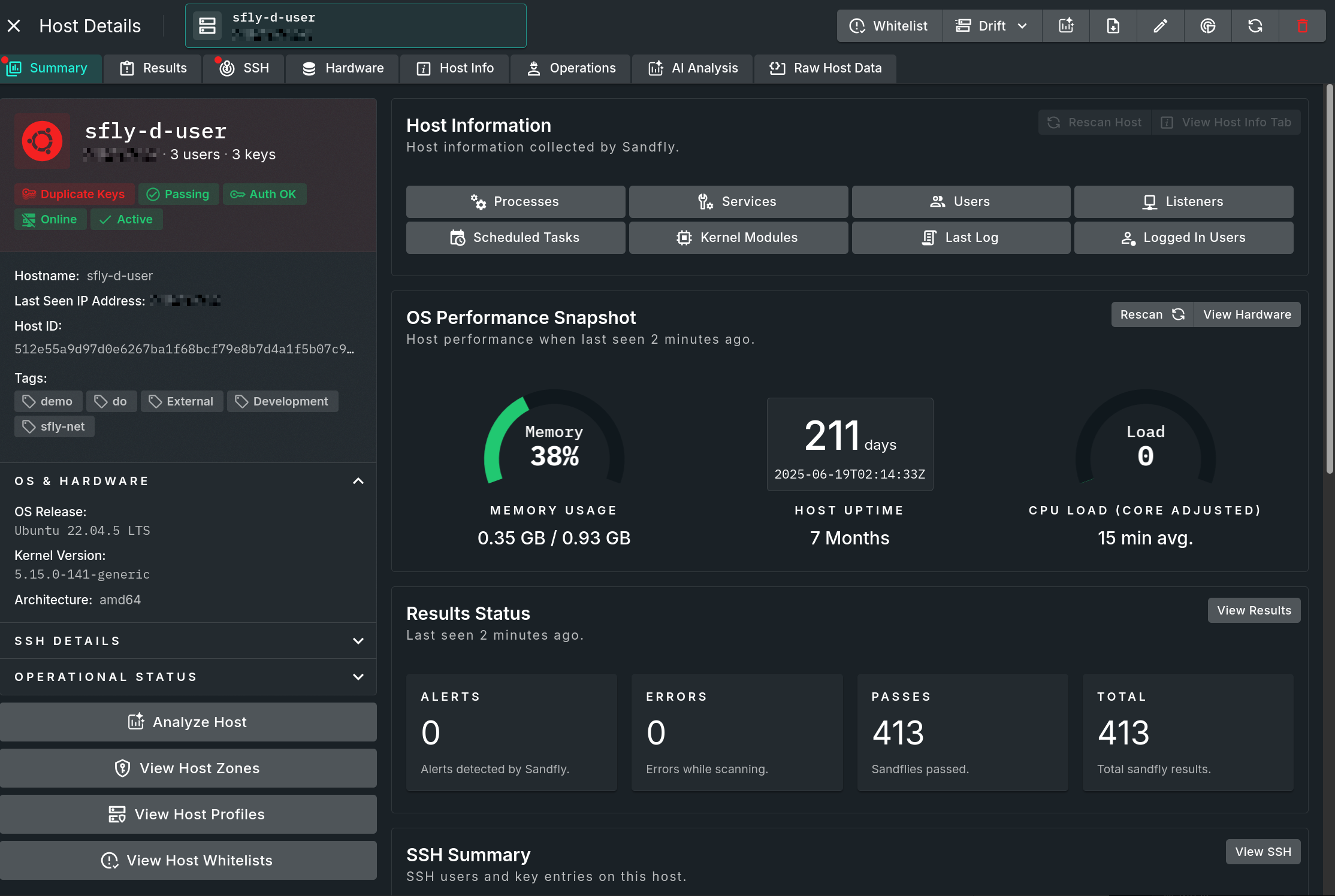
Detailed Host View
Sandfly Hunter
Below an alert is the Sandfly Hunter mode. This mode allows you to search across all hosts for particularly important forensic data in an alert. This forensic data will vary depending on the alert type seen, but includes names, paths, cryptographic hashes and other information that can help you quickly see what other hosts may have that relates to the alert.
For instance, clicking on a suspicious process will show you cryptographic hashes of that process. You can then click on the Sandfly Hunter hash search and Sandfly will show you all hosts running that same process whether or not it generated an alert. Below we have found a suspicious process on one host, but clicking on that hash shows that multiple hosts were seen running that same process without alerts. This kind of search can help identify spread of malicious binaries, users, SSH keys and other important threat hunting data.
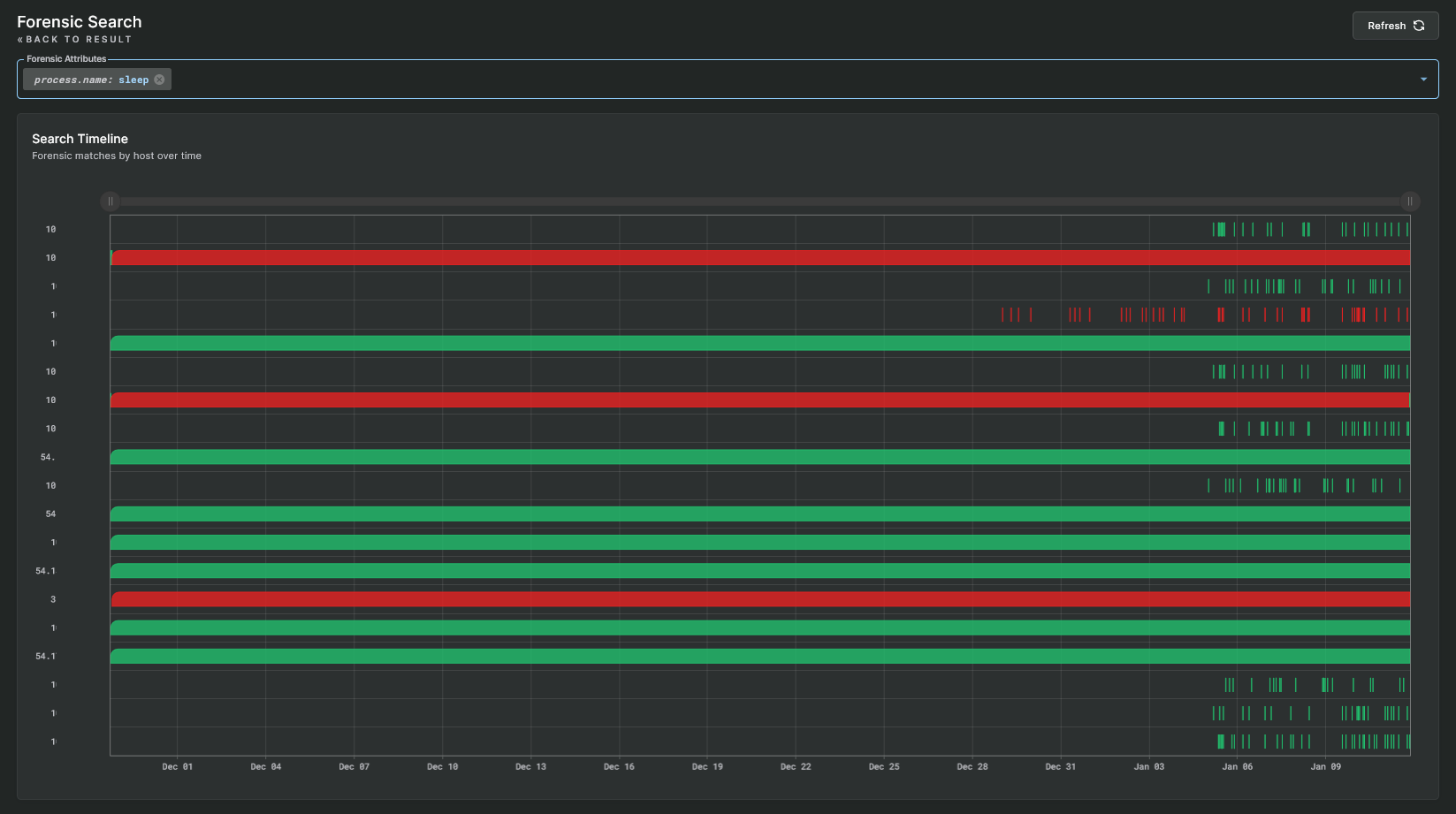
Sandfly Hunter Mode
The Sandfly Hunter is a powerful feature and is discussed in further detail in the Sandfly Hunter section.
Results Action Buttons
Atop each result detail panel are buttons with actions that can be performed on the result. Available actions include:
Recheck
Sometimes you may want to quickly check if an event is still happening on a system. The Recheck button immediately initiates a manual scan, using the host and sandfly from the result, so the host can be checked again to see if the alert reoccurs. If it does, then this can confirm that the alert is still an issue. If you are experiencing a transient alert that you think is a false alarm but not something to be whitelisted, you can use this action to confirm.
Whitelist
Clicking on the Whitelist button opens a form for adding a new rule which can either completely disable a sandfly or apply hash matches that prevents matched results from becoming alerts.
The section on Whitelisting explains this process further.
Profile
Clicking on the Create New Profile button opens a form for creating a new result profile which can be used for drift detection and/or result whitelisting.
Clicking on the Add to Existing button opens a separate form for adding the selected hosts and/or results to an existing result profile.
The section on Result Profiles explains the profiling feature in detail.
Delete
Clicking the Delete button will delete this event and take you back to the results screen.
IMPORTANT: Suspicious Problems Do Not Just Fix ThemselvesComputers are not spontaneous. If a problem is found by Sandfly and then just vanishes it could be a false alarm. But then again, it may not. Suspicious activity that fixes itself is in itself suspicious.
Sandfly and False Alarms
The sandflies that do the investigations are written carefully to not have false alarms. However, if this is your first time running Sandfly it is possible that something in your environment configuration could cause a false alarm.
We suggest you treat any threats detected as real unless you can verify 100% they are not a problem. If you are sure it is a false alarm and it is activating constantly, please see the section on Whitelisting to disable or override the offending module on this host.
After you whitelist the sandfly, please contact us if you think it is a genuine false alarm. We can help diagnose if it is a legitimate false alarm, or just something with your particular environment that cannot be avoided. If we determine it is a problem with the sandfly we will create a fix and get it posted in the next update.
TODO: Contact Us If a Sandfly is Causing False AlarmsIf you find a sandfly that is always causing a false alarm, please let us know. If the false alarm is unique to your environment, it may not be something we can help with. But if it is not unique to your environment, we want to know so we can fix it and make Sandfly as reliable as possible.
MITRE ATT&CK® © 2025 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation.
Updated about 1 month ago