Theory of Operation
Sandfly is an Automated Security and Forensic Investigator
Sandfly provides agentless security for Linux. It does this with an innovative approach that securely connects to endpoints, pushes over investigative code modules (called sandflies), and then obtains results. The results either show the system is compromised in one or more ways, or shows no evidence of compromise.
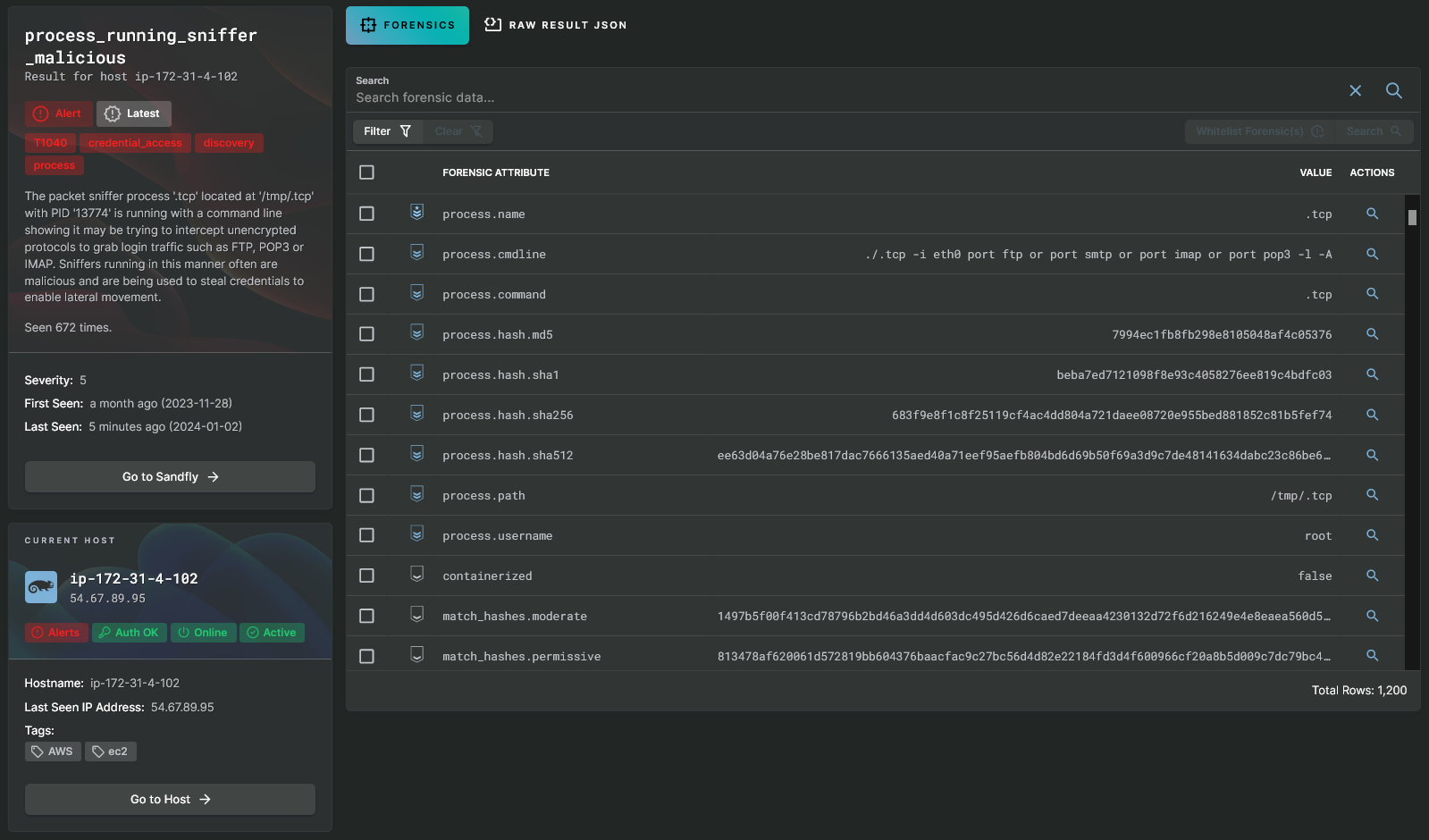
Malicious Sniffer on Linux
Sandfly runs constantly on your network using random schedules and random selection of sandflies to hunt for intruders on your Linux systems. Sandfly functions as a very high performance security investigator searching constantly for trouble. If Sandfly spots anything suspicious, it switches roles and collects data like an expert forensic investigator to reveal exactly what is happening on the remote system.
Additionally, Sandfly can be used as an on-demand security investigator as well. During an incident, use Sandfly to search large numbers of Linux hosts for signs of compromise, or launch spot checks on suspected systems to collect evidence of potential activity.
Updated about 1 month ago