User Investigation
The User Investigation area of SSH Hunter provides information that centers around user aspects of SSH key data that is collected by Sandfly.
Table View
The principle page offers username search capabilities and lists all users with discovered SSH key data in an easy to use table.
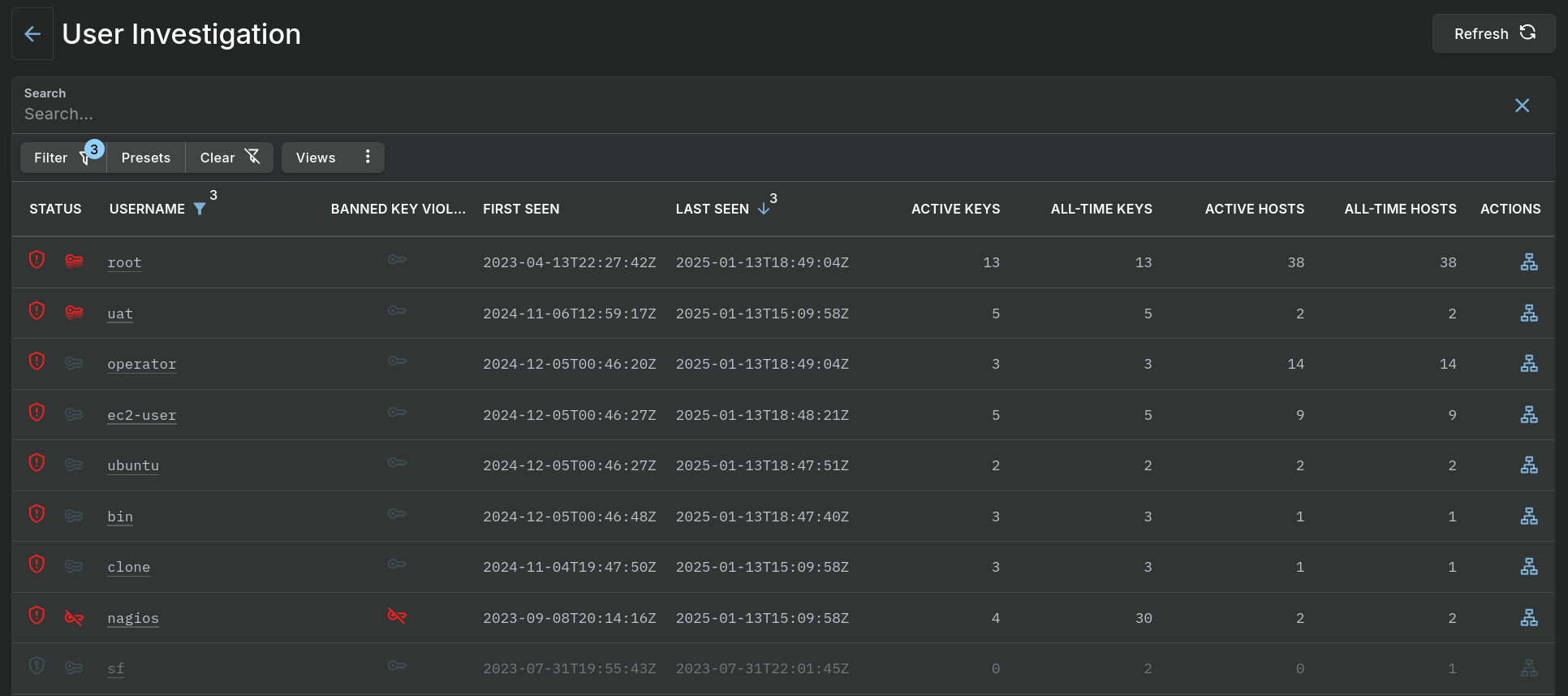
User Investigation - Data Table
Single clicking on a hyperlinked value or double clicking on a row of data, excluding the buttons in the Actions column, will open a panel which contains the details of the associated entry.
Detail View
The Summary tab on the pop-out panel provides an initial view of data on an individual SSH user.
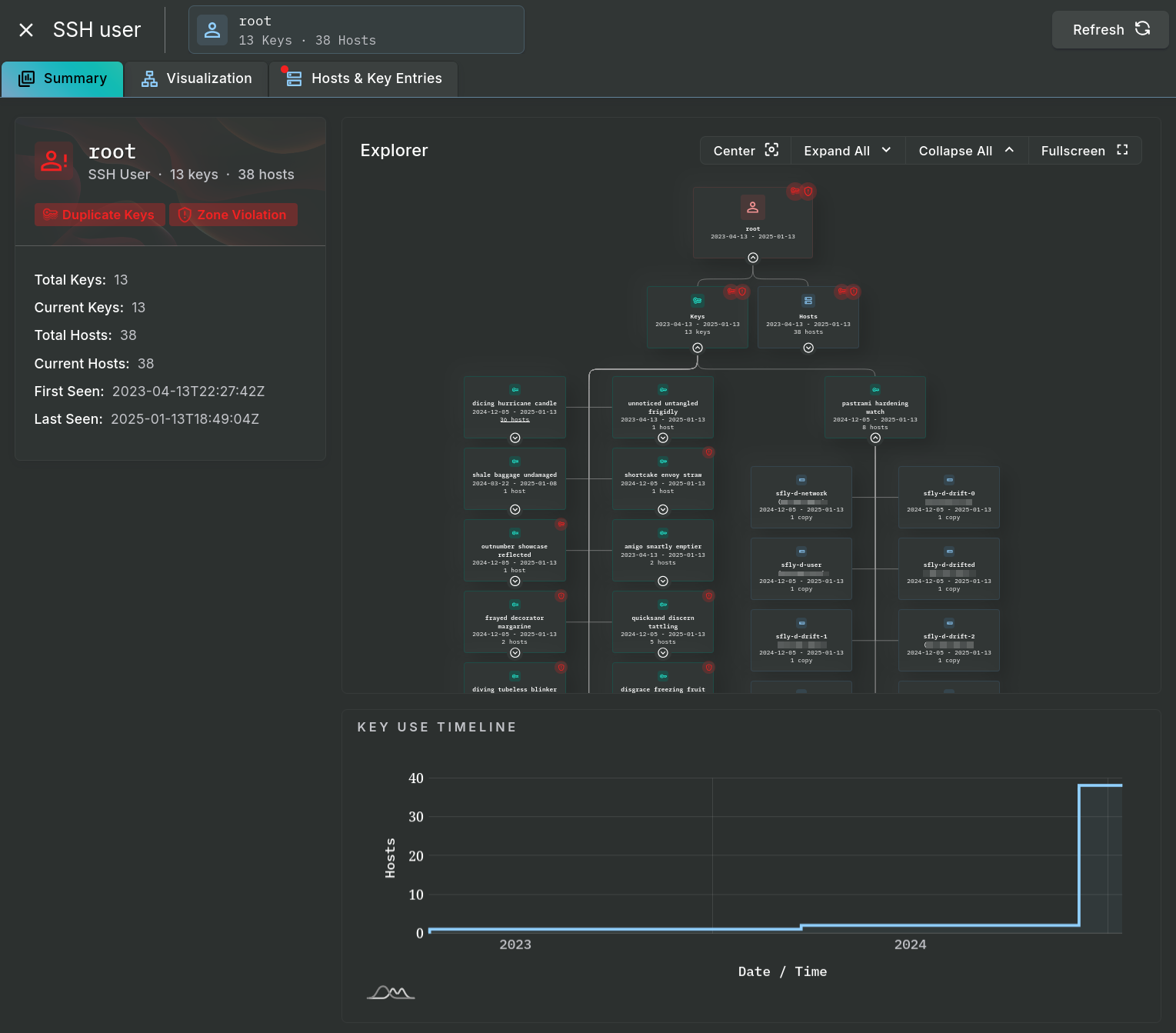
User Investigation - Summary Tab
The Explorer area, found in the Summary tab and a larger, dedicated view under the Visualization tab, can expand and collapse its data and the area can be zoomed or moved around in order to follow the relationship between keys, users, and hosts (some data is expanded in the image above). Below the Explorer is the Key Use Timeline section showing key quantities on the connected hosts over time.
Individual hosts and their key entries are displayed in a table under the Hosts & Key Entries tab.
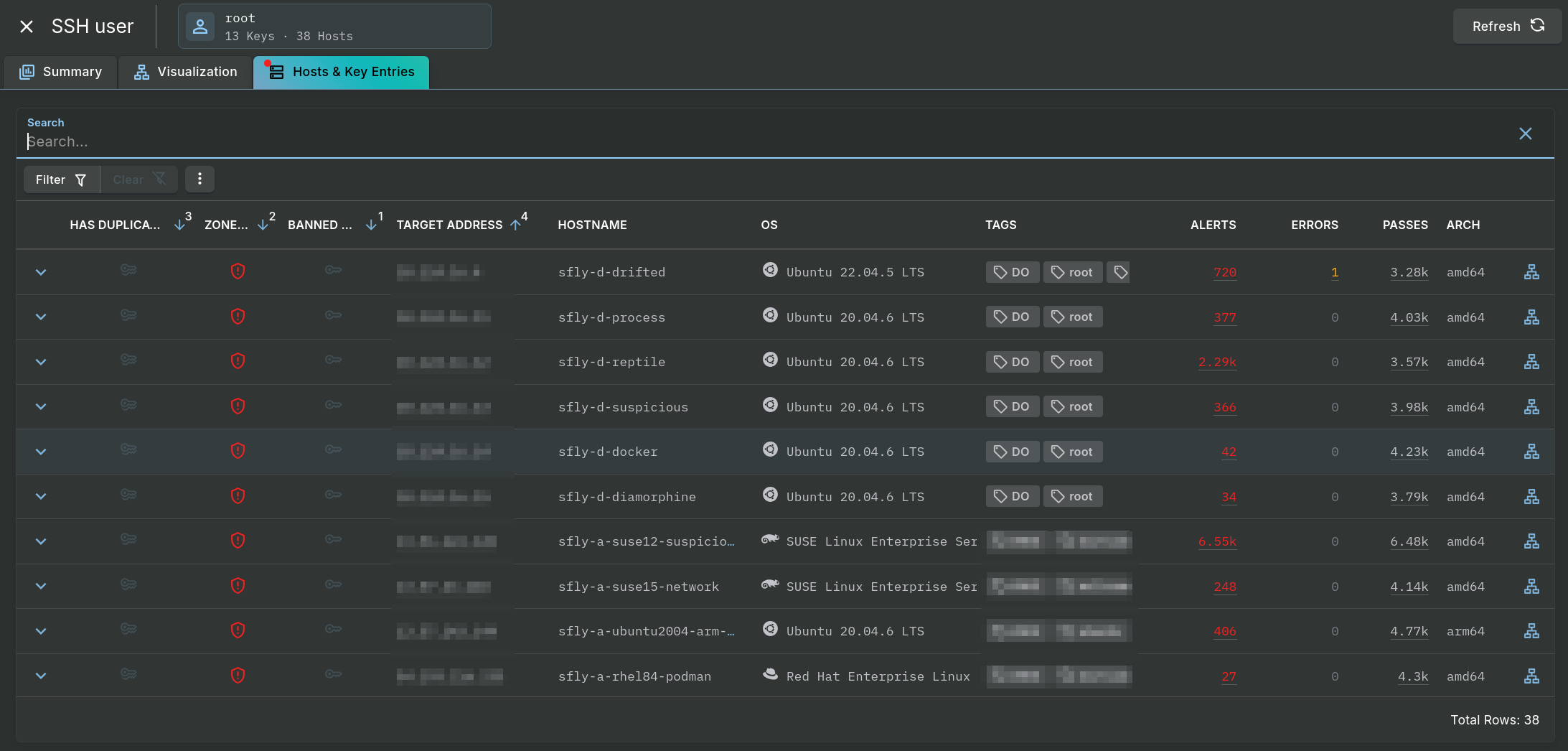
User Investigation - Hosts & Key Entries Tab
Updated about 1 month ago