JunOS Evolved
Juniper's JunOS Evolved is a Linux-based router operating system. As a Linux system that provides direct shell access over SSH with sudo permissions, Sandfly is able to scan it.
JunOS Evolved boots the kernel with IMA (Integrity Measurement Architecture) enforcement enabled, which requires all executable binaries and libraries be signed with a key permitted by the kernel. You may add an IMA signing key to credentials in Sandfly, and Sandfly will sign the scanning binary on the target host using the key you provide.
Setup
To scan a JunOS Evolved router with Sandfly, you need to create an IMA signing key pair, add the public key to the router as a trusted IMA key, create the sandfly user on the router, and create the credential with IMA signing enabled in Sandfly.
Juniper provides documentation for signing third-party binaries at https://www.juniper.net/documentation/us/en/software/junos/overview-evo/topics/topic-map/evo-signing-ima-key.html🡵 ; the instructions below are adapted from that description. We do not recommend generating the key pair on the router itself since that leaves the private key exposed on the device it is meant to protect.
Create an IMA key pair
On a Linux host, run:
openssl req -new \
-newkey rsa:4096 \
-x509 -sha256 \
-days 3650 \
-out ima-cert.x509 -outform DER \
-keyout ima-cert.keyProvide a password to protect the private key at the “Enter PEM pass phrase” prompt.
Answer the certificate details prompts (country, location, company, etc.; the values are unimportant, they are just recorded in the generated certificate).
This will produce “ima-cert.x509”, the public key to install on the router, and “ima-cert.key”, the private key to load into Sandfly.
Add certificate to router
To add the certificate to the JunOS Evolved router, copy the “ima-cert.x509” certificate to the router (e.g. via ftp if it’s enabled, or scp if you have a user for which that works) at a location such as /tmp/ima-cert.x509.
From the JunOS CLI (not the Linux shell), run the command:
request security system-keystore import key-name sandfly-ima-key x509-cert /tmp/ima-cert.x509
Substitute the name “sandfly-ima-key” with whatever you want the key to be called, and the “/tmp/ima-cert.x509” path with the path where you put the certificate file. After the router imports the key, you should receive confirmation information such as:
sandfly@junosevo01> ...sandfly-ima-key x509-cert /tmp/ima-cert.x509
re0:
Key Name: sandfly-ima-key
X509 Cert Path: /etc/ima-ext/sandfly-ima-key/ima-cert.x509
Key SKI: 67240b6a100c0dd89c71873ca5082842fc36341aAdd user to router
To be able to scan the router you will need to add a sandfly user. Sandfly needs to be able to log in over SSH with a user that is class “super-user” and has the shell set to “sh”. JunOS Evolved supports SSH keys for authentication; Sandfly recommends you use them instead of passwords.
An example user configuration for the Sandfly user is:
system {
login {
user sandfly {
uid 2000;
class read-only;
shell sh;
authentication {
ssh-ed25519 "ssh-ed25519 AAAA...public key...GGVd0047";
}
}
}
}To create the above configuration, the following CLI commands may be used:
configure
edit system login user sandfly
set uid 2000
set class read-only
set shell sh
set authentication ssh-ed25519 "ssh-ed25519 AAAA...public key...GGVd0047"
commit and-quitAdd user to sudo configuration
Sandfly requires the ability to use “sudo” to gain elevated privileges. As the root user on the JunOS Evolved system, enter the shell (e.g. start shell from the CLI, or exit the CLI if your root user logs into the shell) and run:
echo "sandfly ALL=(ALL) NOPASSWD: ALL" > /etc/sudoers.d/sandfly
If you assigned the Sandfly user a password in addition to the SSH key, and want to require a password for sudo, remove the “NOPASSWD:” directive from the above command.
Create the credential in Sandfly
Create a new credential in Sandfly. Use the username and SSH key (or password, if that’s how you configured the router) created in the step above.
Enable the “Enable Linux Integrity Measurement Architecture (IMA) signing” toggle, and paste the private key data (from the “ima-cert.key” file) into the IMA Signing Key field, and enter the key passphrase you created with OpenSSL in the IMA Signing Key Password field.
Save the credential.
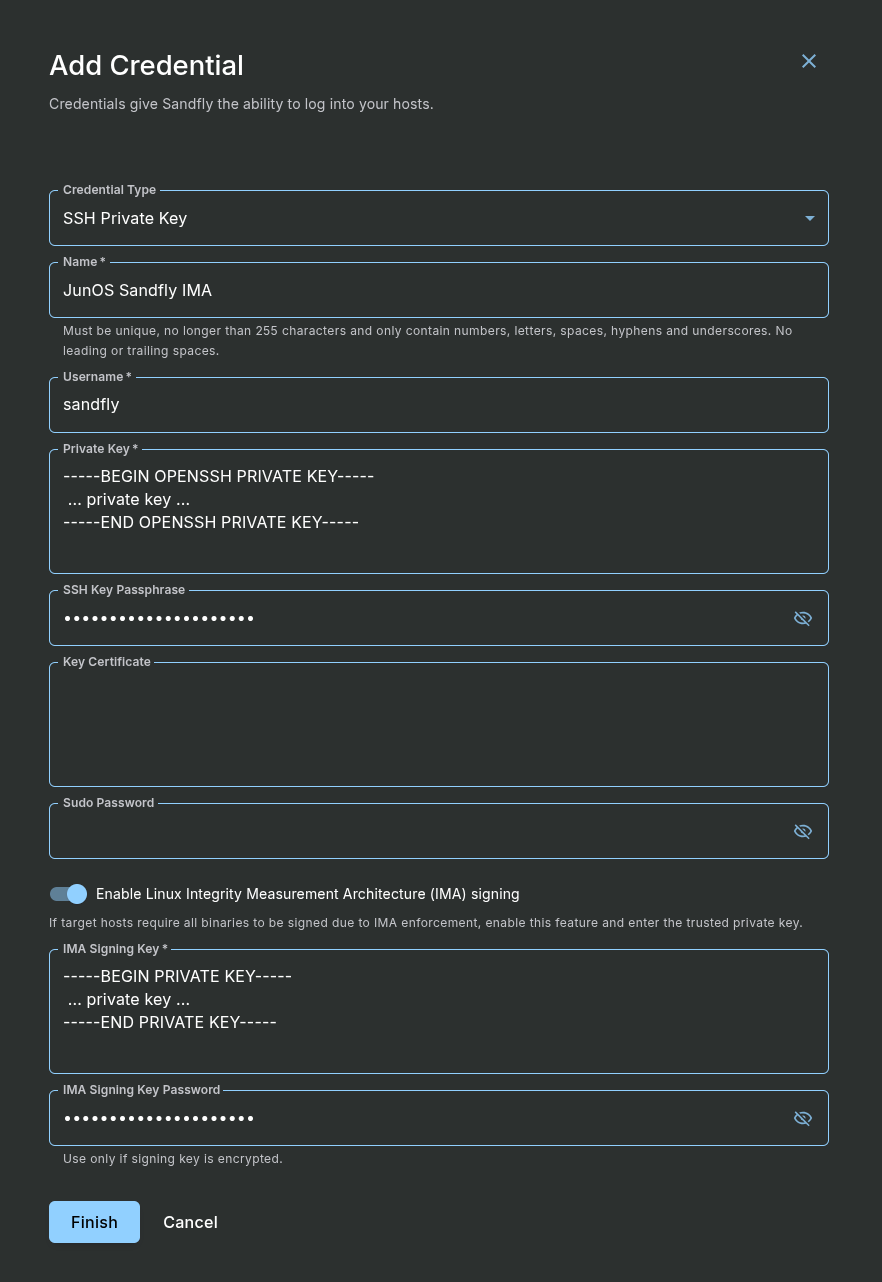
Adding a Credential for JunOS
Finally, add the JunOS Evolved host as a new host in Sandfly, selecting the newly created IMA signing credential.
Updated about 1 month ago