Threat Feeds
Located under Settings in the sidebar, Threat Feeds allow a Sandfly instance to check files, processes, and SSH keys against known-malicious hashes loaded from an external source.
INFO: Upgrade Feature - Threat FeedsThe ability to configure and use Threat Feeds requires an upgraded plan. Please see https://www.sandflysecurity.com/get-sandfly/🡵 for details.
Any time the Sandfly server processes results from sandflies that include file hashes, process hashes, or SSH authorized keys hashes, Sandfly will check the hashes against all of the hashes in the threat feed and create a new alert result if there is a match.
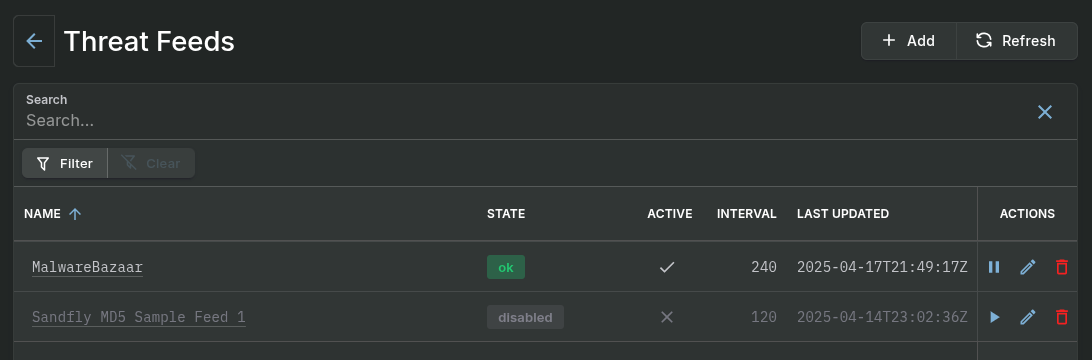
Threat Feeds Main View
When creating a threat feed, you enter the URL that Sandfly should download the list of hashes from. This URL needs to point to a file that is either plain text, or a ZIP file that has one or more plain text files inside of it.
File Requirements
The accepted format of the threat feed file is one hash per line. A hash can be md5, sha1, sha256, or sha512. A file can contain a mix of hash algorithms.
The downloaded file must be less than 100MB. A single threat feed must have fewer than 2.5 million lines.
The hashes from all enabled threat feeds are kept in RAM in the Sandfly server process; there is very little overhead, so the amount of RAM used is essentially the size of the (unzipped) threat feed file, but if you plan on loading many threat feeds, expect the Sandfly server RAM usage to increase by that amount.
Blank lines and lines that begin with a # are ignored. Other lines that do not appear to be a supported hash value will be skipped, but will emit a warning in the Sandfly server log. If there are more than 10 non-blank, non-hash lines, the threat feed will not be loaded and will switch to an error state.
Feed Operations
Sandfly will re-download and re-import threat feeds from the URL based on the configured refresh interval. To force a threat feed to refresh immediately, disable then re-enable it.
There are three server-side sandflies that represent the three types of threat feed matches: process_threat_feed_match, file_threat_feed_match, and user_ssh_authorized_key_threat_feed_match. Running these sandflies will have no effect as they do not generate any results on their own, they are just placeholders for the new results derived from other sandflies (e.g. process or user recon). However, you can deactivate these sandflies to disable the corresponding type of hash check. Additionally, you can create host whitelists if you do not want a particular type of hash check to be done for certain hosts.
Also note that hashes are only checked against threat feeds when results are ingested after a scan. If you add a new threat feed, or if a threat feed adds new hashes, no alerts are generated right away. New alert results will only be created if a future scan includes files/processes/keys that match the new hash list(s).
When configuring threat feeds, you can optionally provide the “Additional Info URL”. If present, the explanation of alert results will include the URL and tell the user there may be more info at the URL. Furthermore, if you include $HASH in the URL, the matching hash that triggered the URL will be inserted into the URL at that point.
Example threat feed settings for the Malware Bazaar database from abuse.ch ( https://bazaar.abuse.ch/🡵 ):
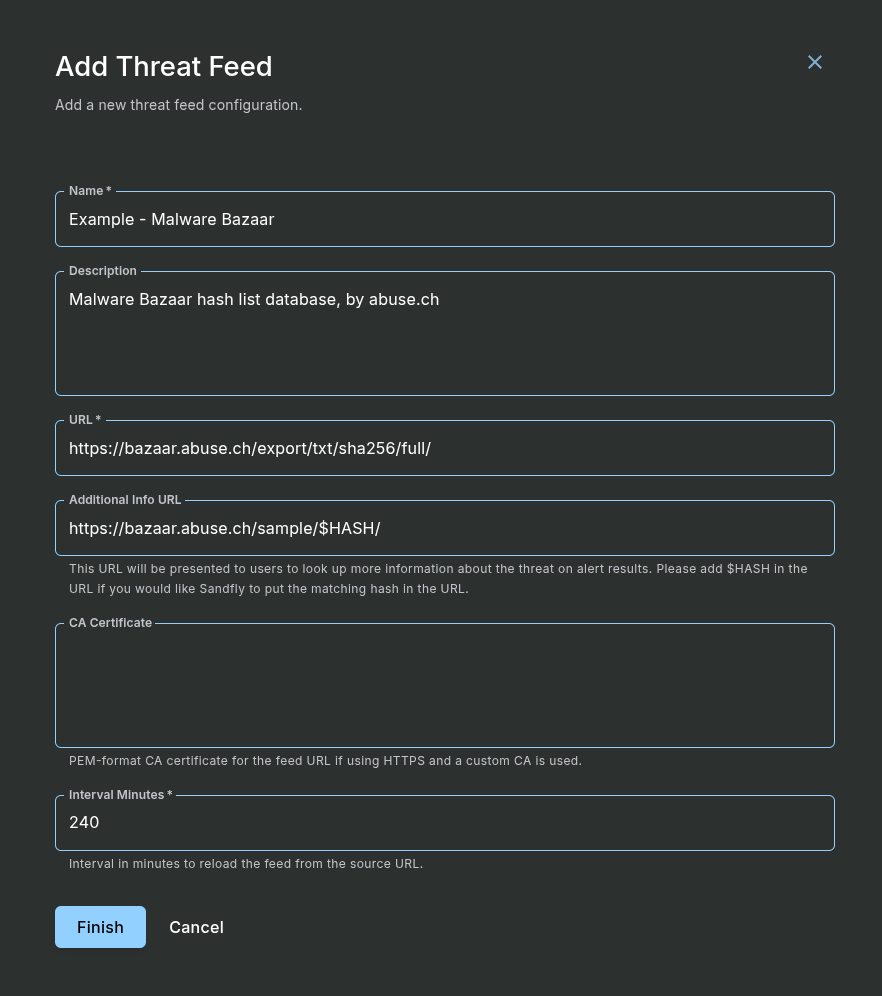
Add Threat Feed Form with Example
Updated about 1 month ago