Key Investigation
The Key Investigation area of SSH Hunter provides information that centers around SSH key data that is collected by Sandfly.
Table View
The principle page offers search capabilities of textual fields and lists all SSH keys, whether discovered or manually added, in an easy to use table.
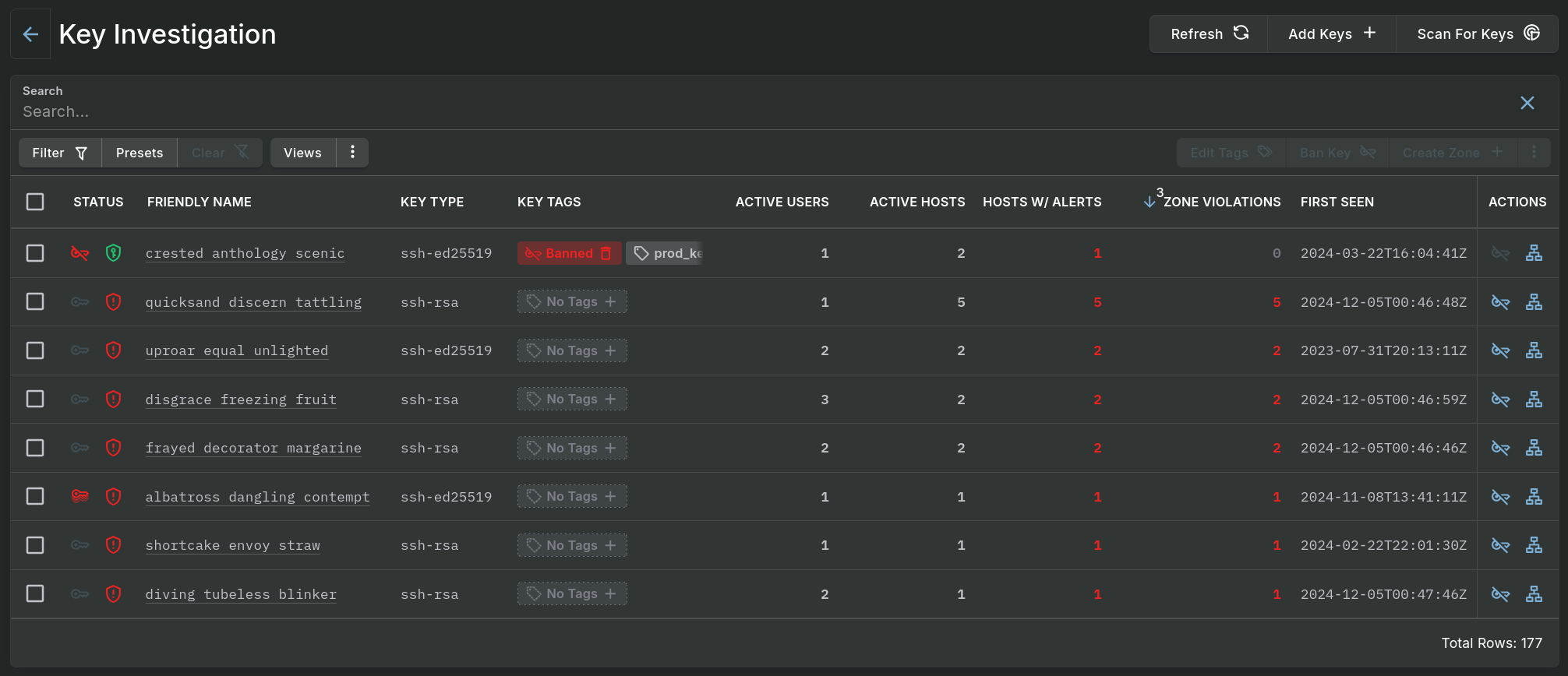
Key Investigation - Data Table
Single clicking on a hyperlinked value or double clicking on a row of data, excluding the checkboxes and Action buttons, will open a panel which contains the details of the associated entry.
Detail View
The Summary tab on the pop-out panel provides an initial view of data on an individual SSH key.
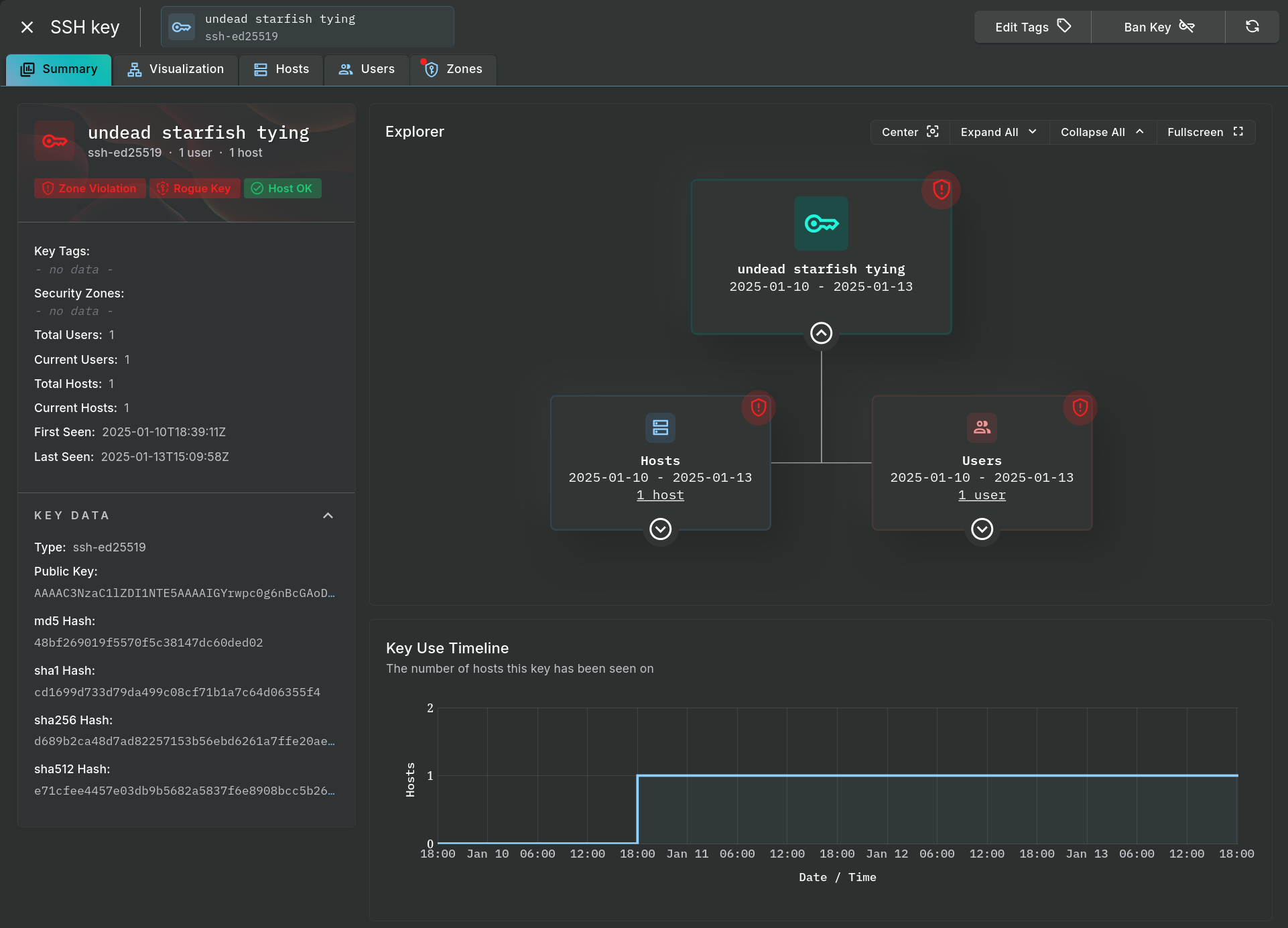
Key Investigation - Summary Tab
The Explorer area, found in the Summary tab and a larger, dedicated view under the Visualization tab, can expand and collapse its data and the area can be zoomed or moved around in order to follow the relationship between keys, users, and hosts. Below the Explorer is the Key Use Timeline section showing key quantities on the connected hosts over time.
Clicking on the Hosts, Users, or Zones tab will provide a table with of the respective data.
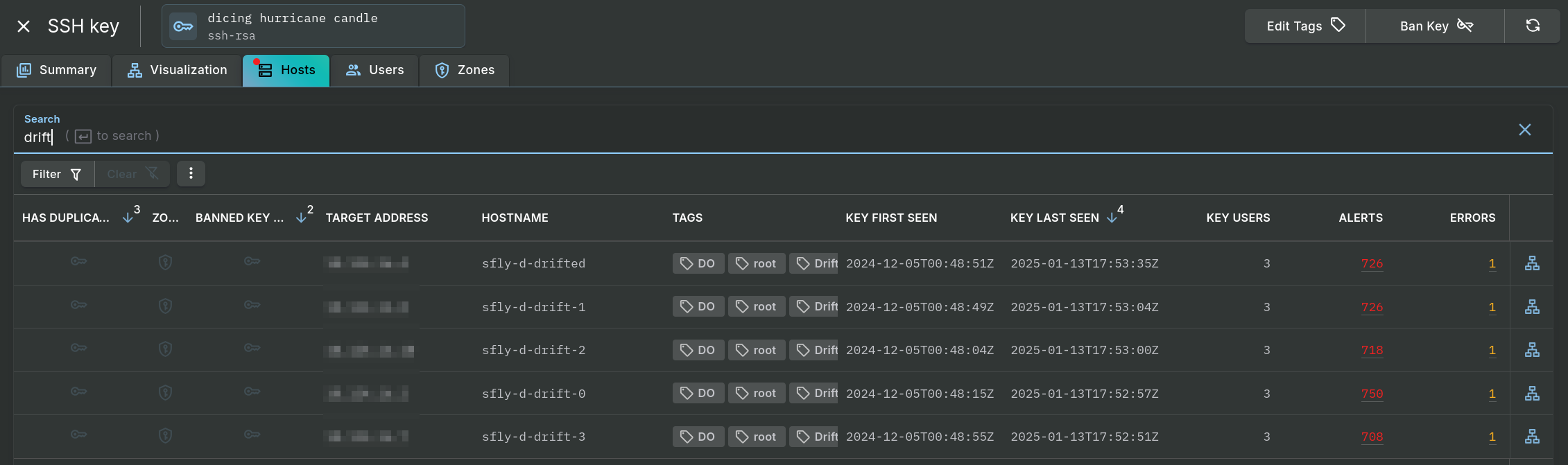
Key Investigation - Hosts Tab
Manually Adding Keys
Normally, the keys listed in the Key Investigation page and the Tag Workbench are the keys Sandfly has found on hosts through scans that include the recon_user_list_all sandfly.
However, this means you can only tag or ban keys that are already on hosts. You may want to watch for known retired or malicious keys that are not currently on hosts and be alerted as soon as such a key shows up.
Or, you may wish to add a set of allowed keys to a Security Zone without first having to add them to the hosts – potentially generating nuisance alerts if you know you are adding new allowed keys to hosts in that zone due to key rotation, new employee hires, etc.
This feature lets you add keys to the system directly instead of having to discover them via scans.
To manually add keys, open the Key Investigation page and then click the Add Keys button found in the top-right corner.
The Add SSH Keys form allows you to paste in SSH public keys, with one key per line. The entries may be copied directly from authorized_keys files and Sandfly will parse out the key itself, or the entries may be just the key without the type and comment fields found in authorized_keys files. You may also use a combination of the two formats in a single operation.
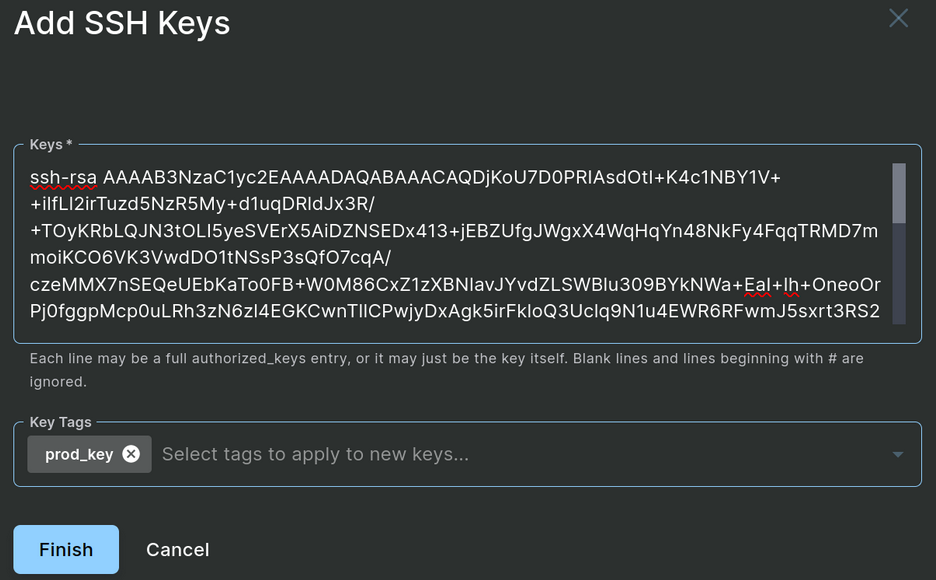
Add SSH Keys Form
Any tags you enter in the Add SSH Keys dialog will be added to the new keys, immediately allowing them in SSH Security Zones that permit the tags. If the key already exists in Sandfly, the provided key tag(s) will be added to the existing key.
Added keys can also be immediately banned simply by adding the “Banned” tag.
Keys which have been added manually, instead of discovered through scans, can be identified by the First Seen and Last Seen dates in the key list being “Never”.
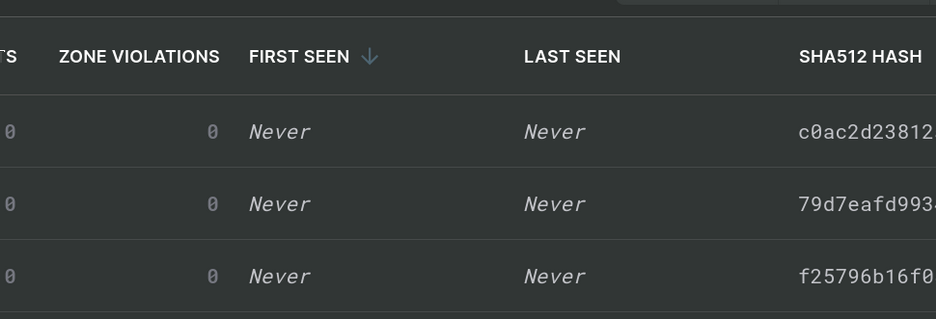
Never Seen Keys
When one of those keys is found on a host, the First / Last Seen dates will be changed to real values and the key will be like any other key Sandfly discovers during scans.
Updated about 1 month ago