Sandfly Auto Response
Sandfly has the ability to actively respond to detected threats. The current version supports killing or suspending process activity that a user wants targeted.
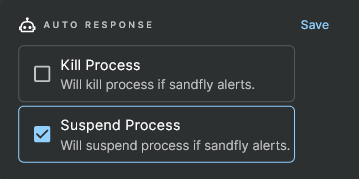
Selecting Auto Response for Detected Linux Attacks
To set a response option, simply to go the main sandfly list and select the sandfly that you want to respond when it activates. The response options are available on the details page, below the details box. In the above example we have set the sandfly to suspend the process if we detect an alert.
Process Threat Response Options
Sandfly has two methods to deal with detected process attacks, suspend or kill.
Suspend Process Response
Often people think the best thing to do when a compromise happens is to kill the process. However, this can cause a lot of lost information and actually hurt proper incident response. Because of this, Sandfly can simply suspend a process it flags as suspicious.
Suspending a process has advantages over simply killing something that looks suspicious. These are:
- The process forensic memory footprint is preserved for analysis.
- You can recover the running binary from memory even if the binary on the disk has been deleted.
- The process still appears to be running if automated malware returns and tries to re-infect the host.
- It can halt the damage of the malware while giving incident responders time to regroup, isolate the host and consider how to approach the problem methodically.
In general, unless you are sure the process needs to be killed we recommend you suspend it so it can be investigated. Once you see what is going on you can isolate the system and take further actions.
Kill Process Response
When you set Sandfly to kill a suspicious process we will terminate the process immediately on the host. While this will stop the process in question, it may also cause any forensic data it has in memory to be immediately lost.
In general, we do not recommend that you kill any suspicious process until it has been investigated and evidence preserved. If you are sure the process is something you do not want to deal with, then killing it may still be a good option.
Updated 26 days ago