Security Zones
SSH Security Zones let you select a group of hosts, by host tags, and declare that they belong in a zone. You may then select SSH public keys, by tags, that are allowed on hosts inside that zone.
If a host is in a zone and a key that is not permitted by the zone is found on the host, Sandfly will generate an alert result during scans and indicate zone violations in the SSH Hunter pages in the Sandfly User Interface (UI).
Key status icons
In addition to alerts from future scans, real-time status is shown throughout the SSH Hunter views in the UI. For example, the Key Investigation, User Investigation, and Host Investigation lists all have status icons indicating a zone violation is occurring related to the key/user/host (indicated by a red shield icon), and violations are indicated in the detail pages and graph views of the SSH Security Zones.
Various icons in the Key Investigation list indicate how keys are currently involved with security zones:
A green shield means that they key is permitted in at least one security zone, and is not currently found in any other security zones causing a violation.
Lack of a shield (dim / dashed-line icon) means that the key is not permitted in any security zones, and has not been found on any host that is in a security zone. This is the “default state” when non-zoned keys are only found on non-zoned hosts.
A red dashed-line shield icon indicates that the key is not permitted by any security zones, but it was found on a host that is in a security zone.
Finally, a solid red shield means that the key is both permitted in one or more security zones, and ALSO has been found on a host in another security zone that this key is not permitted in.
Zone Status
The SSH Security Zones section lists all of the created zones along with presenting a quick overview of the integrity of SSH public key access to your network.
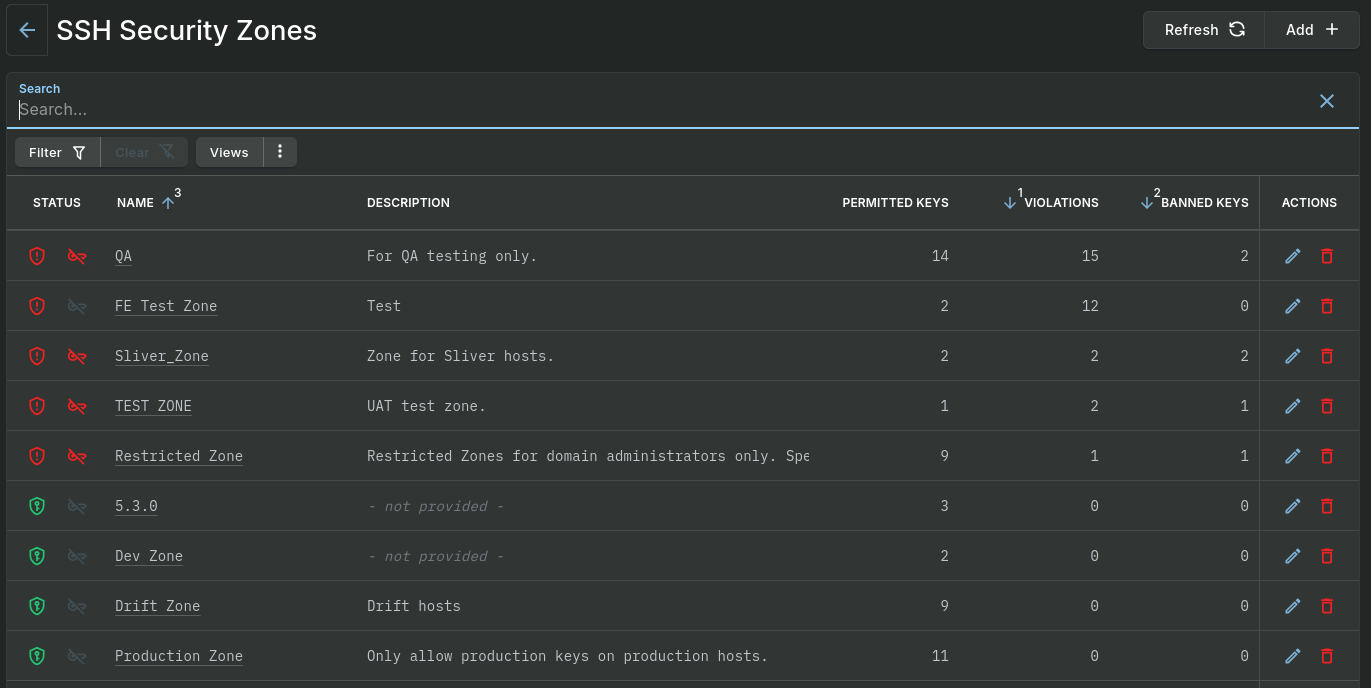
A red shield icon means that the zone has violations – that is, one or more hosts in the zone have an SSH key that is not permitted in the zone. A red key icon mean that the zone contains one or more banned keys. Click on a zone for more details.
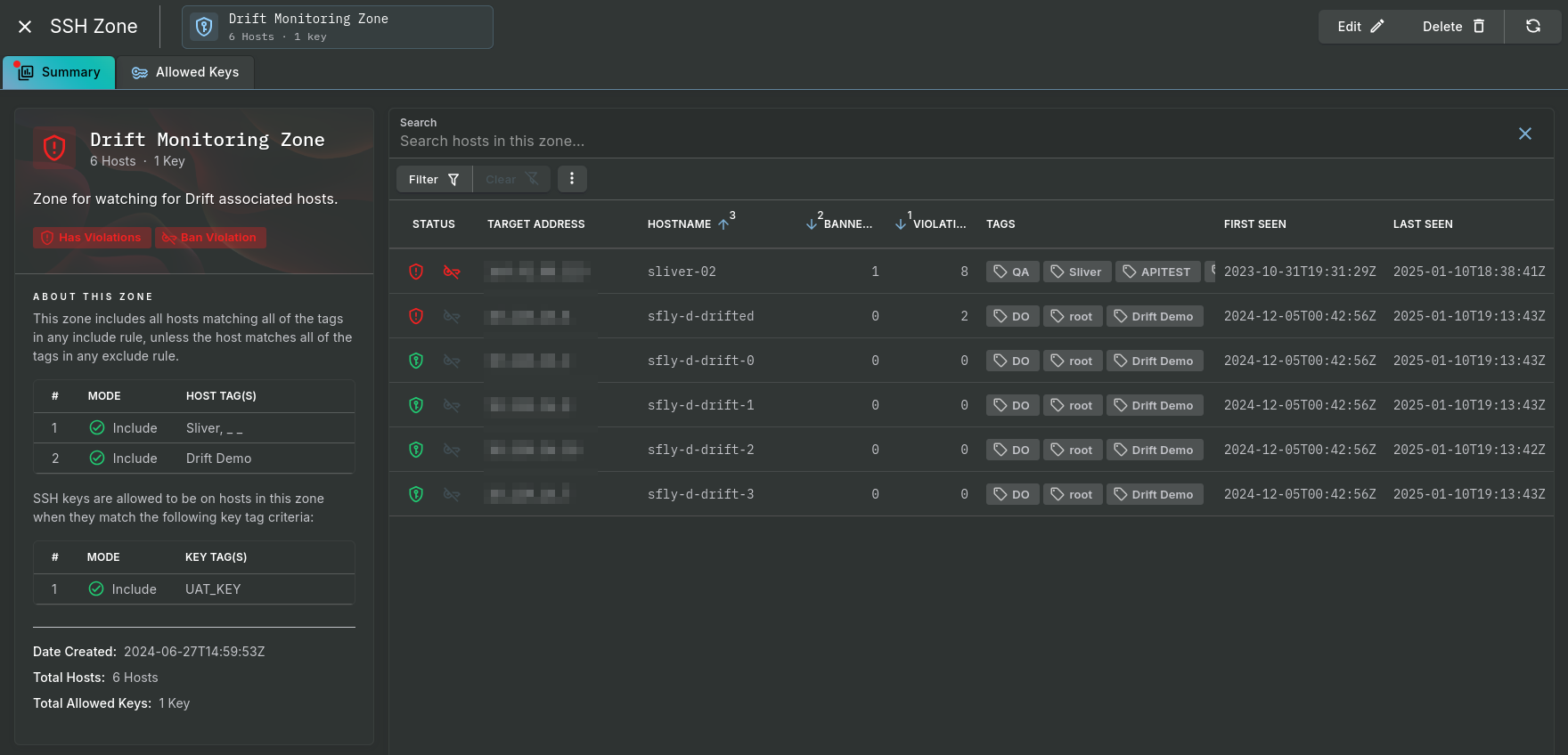
A zone's Summary tab shows all the hosts in the zone that matches the criteria. When a host has an SSH key that is not permitted in the zone and/or is banned, an associated red icon is displayed in the "Status" column.
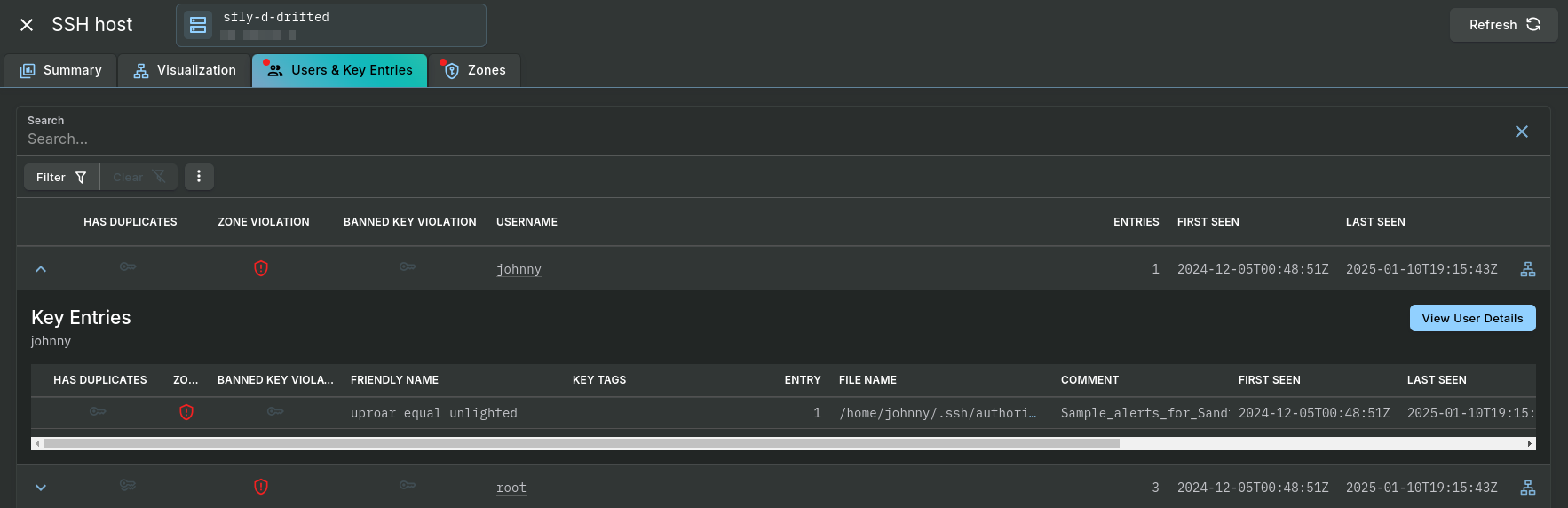
Clicking on a host will open the SSH Host panel. Under the Users & Key Entries tab you can see the specific users and the entries in their authorized_keys files that are in violation of the zone:
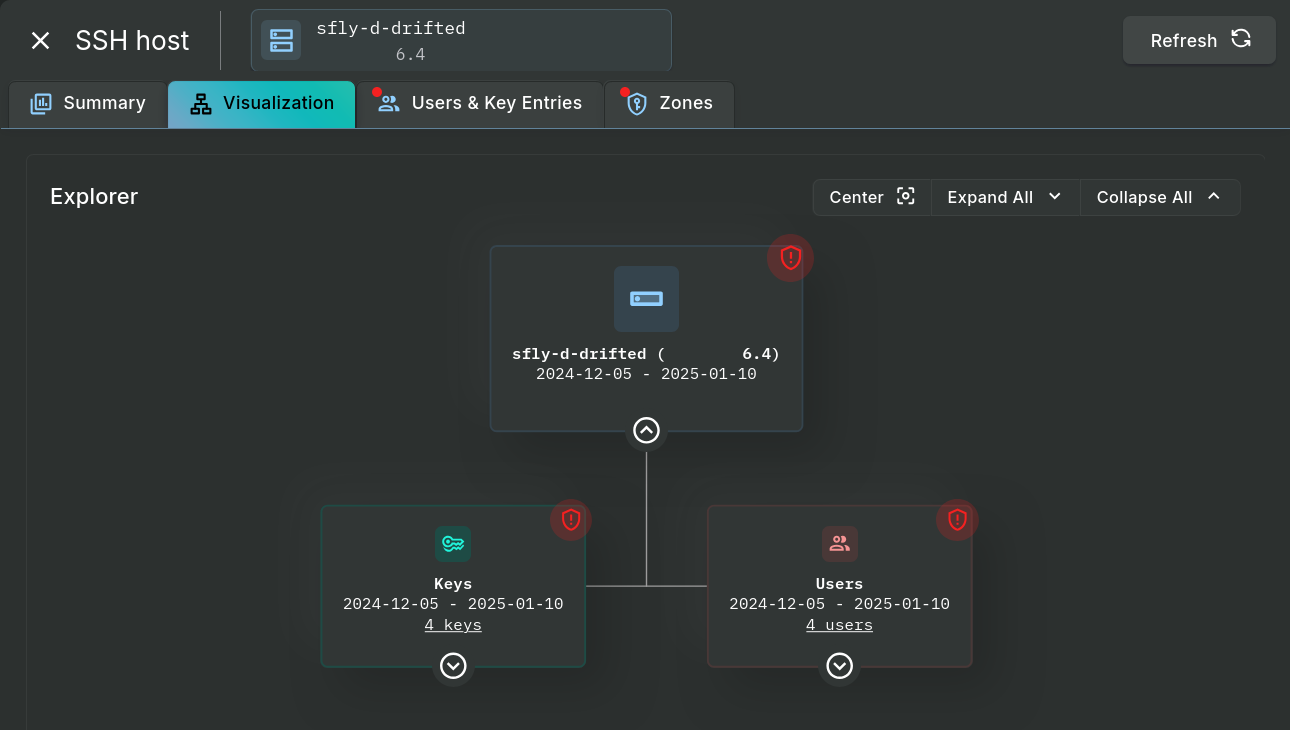
The Explorer view, under the Visualization tab, also show a zone violation icon if the tree node or one of its descendants contains a zone violation:
VIDEO SPOTLIGHT: SSH Security Zones - Full demo of how to track, secure and monitor SSH keys on Linux agentlessly.
Visit Sandfly Security's YouTube Channel for all of our videos.
Updated about 1 month ago